|
#dig mail.ru ns

l3script: dig: command not found |
| /l3/users/igor-public/vncdemo/root :1 :2 :3 :4 :5 :6 |
|
|
#apt-get install bind-utils

Reading package lists... Done Building dependency tree Reading state information... Done E: Couldn't find package bind-utils |
|
#apt-get install dnsutils
Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: python2.4-minimal python2.4 libttf2 cpp-4.2 Use 'apt-get autoremove' to remove them. The following extra packages will be installed: libbind9-40 libcap2 libdns43 libisc44 libisccc40 libisccfg40 liblwres40 Suggested packages: rblcheck ... Selecting previously deselected package dnsutils. Unpacking dnsutils (from .../dnsutils_1%3a9.5.0.dfsg.P2-5_i386.deb) ... Setting up libcap2 (2.11-2) ... Setting up libisc44 (1:9.5.0.dfsg.P2-5) ... Setting up libdns43 (1:9.5.0.dfsg.P2-5) ... Setting up libisccc40 (1:9.5.0.dfsg.P2-5) ... Setting up libisccfg40 (1:9.5.0.dfsg.P2-5) ... Setting up libbind9-40 (1:9.5.0.dfsg.P2-5) ... Setting up liblwres40 (1:9.5.0.dfsg.P2-5) ... Setting up dnsutils (1:9.5.0.dfsg.P2-5) ... |
|
#dig mail.ru ns
; <<>> DiG 9.5.0-P2 <<>> mail.ru ns ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 44584 ;; flags: qr rd ra; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;mail.ru. IN NS ;; ANSWER SECTION: mail.ru. 3600 IN NS ns4.mail.ru. mail.ru. 3600 IN NS ns3.mail.ru. mail.ru. 3600 IN NS ns1.mail.ru. mail.ru. 3600 IN NS ns.mail.ru. mail.ru. 3600 IN NS ns2.mail.ru. mail.ru. 3600 IN NS ns5.mail.ru. ;; Query time: 397 msec ;; SERVER: 10.0.35.1#53(10.0.35.1) ;; WHEN: Wed Dec 17 14:21:39 2008 ;; MSG SIZE rcvd: 132 |
|
#dig mail.ru ns
; <<>> DiG 9.5.0-P2 <<>> mail.ru ns ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 26636 ;; flags: qr rd ra; QUERY: 1, ANSWER: 6, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;mail.ru. IN NS ;; ANSWER SECTION: mail.ru. 3593 IN NS ns1.mail.ru. mail.ru. 3593 IN NS ns3.mail.ru. mail.ru. 3593 IN NS ns4.mail.ru. mail.ru. 3593 IN NS ns2.mail.ru. mail.ru. 3593 IN NS ns.mail.ru. mail.ru. 3593 IN NS ns5.mail.ru. ;; Query time: 1 msec ;; SERVER: 10.0.35.1#53(10.0.35.1) ;; WHEN: Wed Dec 17 14:21:46 2008 ;; MSG SIZE rcvd: 132 |
|
#dig nt.ua ns
; <<>> DiG 9.5.0-P2 <<>> nt.ua ns ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35664 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 2 ;; QUESTION SECTION: ;nt.ua. IN NS ;; ANSWER SECTION: nt.ua. 5407 IN NS ns2.tsua.net. nt.ua. 5407 IN NS stream.tsua.net. ;; ADDITIONAL SECTION: ns2.tsua.net. 5407 IN A 212.40.34.10 stream.tsua.net. 5407 IN A 212.40.34.157 ;; Query time: 1 msec ;; SERVER: 10.0.35.1#53(10.0.35.1) ;; WHEN: Wed Dec 17 14:22:03 2008 ;; MSG SIZE rcvd: 102 |
|
#dig nt.ua ns
; <<>> DiG 9.5.0-P2 <<>> nt.ua ns ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 49200 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 2 ;; QUESTION SECTION: ;nt.ua. IN NS ;; ANSWER SECTION: nt.ua. 5382 IN NS ns2.tsua.net. nt.ua. 5382 IN NS stream.tsua.net. ;; ADDITIONAL SECTION: ns2.tsua.net. 5382 IN A 212.40.34.10 stream.tsua.net. 5382 IN A 212.40.34.157 ;; Query time: 0 msec ;; SERVER: 10.0.35.1#53(10.0.35.1) ;; WHEN: Wed Dec 17 14:22:28 2008 ;; MSG SIZE rcvd: 102 |
|
#dig ids.ua mx
; <<>> DiG 9.5.0-P2 <<>> ids.ua mx ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 48310 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;ids.ua. IN MX ;; ANSWER SECTION: ids.ua. 3600 IN MX 10 mail.ids.ua. ;; AUTHORITY SECTION: ids.ua. 3600 IN NS ns.ids.ua. ids.ua. 3600 IN NS nss.sovamua.com. ;; ADDITIONAL SECTION: mail.ids.ua. 3600 IN A 212.82.195.122 nss.sovamua.com. 158123 IN A 62.64.120.244 ;; Query time: 162 msec ;; SERVER: 10.0.35.1#53(10.0.35.1) ;; WHEN: Wed Dec 17 14:23:53 2008 ;; MSG SIZE rcvd: 123 |
|
#dig @mail.ids.ua google.ru a
; <<>> DiG 9.5.0-P2 <<>> @mail.ids.ua google.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 47141 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 13, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;google.ru. IN A ;; AUTHORITY SECTION: ... . 518400 IN NS A.ROOT-SERVERS.NET. . 518400 IN NS B.ROOT-SERVERS.NET. . 518400 IN NS C.ROOT-SERVERS.NET. . 518400 IN NS D.ROOT-SERVERS.NET. . 518400 IN NS E.ROOT-SERVERS.NET. . 518400 IN NS F.ROOT-SERVERS.NET. ;; Query time: 17 msec ;; SERVER: 212.82.195.122#53(212.82.195.122) ;; WHEN: Wed Dec 17 14:24:26 2008 ;; MSG SIZE rcvd: 238 |
|
#dig elektrod.com.ua ns
; <<>> DiG 9.5.0-P2 <<>> elektrod.com.ua ns ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19377 ;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 2 ;; QUESTION SECTION: ;elektrod.com.ua. IN NS ;; ANSWER SECTION: elektrod.com.ua. 43200 IN NS ns2.dns.com.ua. elektrod.com.ua. 43200 IN NS ns.dns.com.ua. ;; ADDITIONAL SECTION: ns.dns.com.ua. 3488 IN A 62.149.2.8 ns2.dns.com.ua. 3488 IN A 195.149.112.1 ;; Query time: 19 msec ;; SERVER: 10.0.35.1#53(10.0.35.1) ;; WHEN: Wed Dec 17 14:27:25 2008 ;; MSG SIZE rcvd: 104 |
|
#dig elektrod.com.ua mx
; <<>> DiG 9.5.0-P2 <<>> elektrod.com.ua mx ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 6389 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;elektrod.com.ua. IN MX ;; ANSWER SECTION: elektrod.com.ua. 43200 IN MX 10 mx1.mirohost.net. ;; AUTHORITY SECTION: elektrod.com.ua. 43194 IN NS ns.dns.com.ua. elektrod.com.ua. 43194 IN NS ns2.dns.com.ua. ;; ADDITIONAL SECTION: ns.dns.com.ua. 3482 IN A 62.149.2.8 ns2.dns.com.ua. 3482 IN A 195.149.112.1 ;; Query time: 124 msec ;; SERVER: 10.0.35.1#53(10.0.35.1) ;; WHEN: Wed Dec 17 14:27:32 2008 ;; MSG SIZE rcvd: 136 |
|
#dig uz.gov.ua mx
; <<>> DiG 9.5.0-P2 <<>> uz.gov.ua mx ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 54606 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 3, ADDITIONAL: 2 ;; QUESTION SECTION: ;uz.gov.ua. IN MX ;; ANSWER SECTION: uz.gov.ua. 10800 IN MX 10 relay.uz.gov.ua. ;; AUTHORITY SECTION: uz.gov.ua. 10800 IN NS ns.secondary.net.ua. uz.gov.ua. 10800 IN NS ns.uz.gov.ua. uz.gov.ua. 10800 IN NS ns2.uz.gov.ua. ;; ADDITIONAL SECTION: relay.uz.gov.ua. 10800 IN A 195.149.70.22 ns.secondary.net.ua. 64975 IN A 195.149.112.1 ;; Query time: 85 msec ;; SERVER: 10.0.35.1#53(10.0.35.1) ;; WHEN: Wed Dec 17 14:27:55 2008 ;; MSG SIZE rcvd: 147 |
|
#dig @relay.uz.gov.ua google.ru a
|
|
#dig @ns2.uz.gov.ua google.ru a
; <<>> DiG 9.5.0-P2 <<>> @ns2.uz.gov.ua google.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 20826 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 4, ADDITIONAL: 4 ;; QUESTION SECTION: ;google.ru. IN A ;; ANSWER SECTION: google.ru. 1800 IN A 66.249.93.104 ... google.ru. 345600 IN NS ns4.google.com. ;; ADDITIONAL SECTION: ns1.google.com. 297662 IN A 216.239.32.10 ns2.google.com. 297662 IN A 216.239.34.10 ns3.google.com. 297662 IN A 216.239.36.10 ns4.google.com. 297662 IN A 216.239.38.10 ;; Query time: 198 msec ;; SERVER: 195.149.70.30#53(195.149.70.30) ;; WHEN: Wed Dec 17 14:28:34 2008 ;; MSG SIZE rcvd: 221 |
|
#dig @ns.uz.gov.ua google.ru a
; <<>> DiG 9.5.0-P2 <<>> @ns.uz.gov.ua google.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 34996 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 4, ADDITIONAL: 4 ;; QUESTION SECTION: ;google.ru. IN A ;; ANSWER SECTION: google.ru. 1800 IN A 66.249.93.104 ... google.ru. 345600 IN NS ns4.google.com. ;; ADDITIONAL SECTION: ns1.google.com. 55778 IN A 216.239.32.10 ns2.google.com. 83330 IN A 216.239.34.10 ns3.google.com. 83330 IN A 216.239.36.10 ns4.google.com. 83330 IN A 216.239.38.10 ;; Query time: 165 msec ;; SERVER: 195.149.70.20#53(195.149.70.20) ;; WHEN: Wed Dec 17 14:28:40 2008 ;; MSG SIZE rcvd: 221 |
|
#dig @ns.uz.gov.ua odnoklassniki.ua a
; <<>> DiG 9.5.0-P2 <<>> @ns.uz.gov.ua odnoklassniki.ua a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38216 ;; flags: qr rd ra; QUERY: 1, ANSWER: 8, AUTHORITY: 3, ADDITIONAL: 0 ;; QUESTION SECTION: ;odnoklassniki.ua. IN A ;; ANSWER SECTION: odnoklassniki.ua. 300 IN A 195.222.187.87 ... odnoklassniki.ua. 300 IN A 212.119.216.5 odnoklassniki.ua. 300 IN A 212.119.216.6 ;; AUTHORITY SECTION: odnoklassniki.ua. 300 IN NS ns.videogaga.ru. odnoklassniki.ua. 300 IN NS ns.odnoklassniki.ua. odnoklassniki.ua. 300 IN NS ns1.odnoklassniki.ua. ;; Query time: 332 msec ;; SERVER: 195.149.70.20#53(195.149.70.20) ;; WHEN: Wed Dec 17 14:29:02 2008 ;; MSG SIZE rcvd: 226 |
|
#dig @ns.uz.gov.ua mail.ru a
; <<>> DiG 9.5.0-P2 <<>> @ns.uz.gov.ua mail.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 20168 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 6, ADDITIONAL: 0 ;; QUESTION SECTION: ;mail.ru. IN A ;; ANSWER SECTION: mail.ru. 3600 IN A 194.67.57.26 ... mail.ru. 3600 IN NS ns.mail.ru. mail.ru. 3600 IN NS ns1.mail.ru. mail.ru. 3600 IN NS ns2.mail.ru. mail.ru. 3600 IN NS ns3.mail.ru. mail.ru. 3600 IN NS ns4.mail.ru. mail.ru. 3600 IN NS ns5.mail.ru. ;; Query time: 193 msec ;; SERVER: 195.149.70.20#53(195.149.70.20) ;; WHEN: Wed Dec 17 14:29:13 2008 ;; MSG SIZE rcvd: 180 |
|
#dig @ns.uz.gov.ua google.ru a
; <<>> DiG 9.5.0-P2 <<>> @ns.uz.gov.ua google.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 62023 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 4, ADDITIONAL: 4 ;; QUESTION SECTION: ;google.ru. IN A ;; ANSWER SECTION: google.ru. 1741 IN A 216.239.59.104 ... google.ru. 345541 IN NS ns3.google.com. ;; ADDITIONAL SECTION: ns1.google.com. 55719 IN A 216.239.32.10 ns2.google.com. 83271 IN A 216.239.34.10 ns3.google.com. 83271 IN A 216.239.36.10 ns4.google.com. 83271 IN A 216.239.38.10 ;; Query time: 14 msec ;; SERVER: 195.149.70.20#53(195.149.70.20) ;; WHEN: Wed Dec 17 14:29:39 2008 ;; MSG SIZE rcvd: 221 |
|
#dig @ns.uz.gov.ua vkontakte.ru a
; <<>> DiG 9.5.0-P2 <<>> @ns.uz.gov.ua vkontakte.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 31116 ;; flags: qr rd ra; QUERY: 1, ANSWER: 18, AUTHORITY: 3, ADDITIONAL: 0 ;; QUESTION SECTION: ;vkontakte.ru. IN A ;; ANSWER SECTION: vkontakte.ru. 900 IN A 93.186.224.233 ... vkontakte.ru. 900 IN A 93.186.227.125 vkontakte.ru. 900 IN A 93.186.227.126 ;; AUTHORITY SECTION: vkontakte.ru. 900 IN NS ns1.vkontakte.ru. vkontakte.ru. 900 IN NS ns2.vkontakte.ru. vkontakte.ru. 900 IN NS ns3.vkontakte.ru. ;; Query time: 151 msec ;; SERVER: 195.149.70.20#53(195.149.70.20) ;; WHEN: Wed Dec 17 14:29:59 2008 ;; MSG SIZE rcvd: 372 |
|
#dig @ns.uz.gov.ua vkontakte.ru a
; <<>> DiG 9.5.0-P2 <<>> @ns.uz.gov.ua vkontakte.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 54008 ;; flags: qr rd ra; QUERY: 1, ANSWER: 18, AUTHORITY: 3, ADDITIONAL: 0 ;; QUESTION SECTION: ;vkontakte.ru. IN A ;; ANSWER SECTION: vkontakte.ru. 876 IN A 93.186.227.126 ... vkontakte.ru. 876 IN A 93.186.227.124 vkontakte.ru. 876 IN A 93.186.227.125 ;; AUTHORITY SECTION: vkontakte.ru. 876 IN NS ns3.vkontakte.ru. vkontakte.ru. 876 IN NS ns1.vkontakte.ru. vkontakte.ru. 876 IN NS ns2.vkontakte.ru. ;; Query time: 11 msec ;; SERVER: 195.149.70.20#53(195.149.70.20) ;; WHEN: Wed Dec 17 14:30:22 2008 ;; MSG SIZE rcvd: 372 |
|
#dig @ns.uz.gov.ua yandex.ru a
; <<>> DiG 9.5.0-P2 <<>> @ns.uz.gov.ua yandex.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 43016 ;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 4, ADDITIONAL: 0 ;; QUESTION SECTION: ;yandex.ru. IN A ;; ANSWER SECTION: yandex.ru. 10800 IN A 77.88.21.11 ... yandex.ru. 10800 IN A 213.180.204.11 ;; AUTHORITY SECTION: yandex.ru. 345600 IN NS ns1.yandex.ru. yandex.ru. 345600 IN NS ns2.yandex.ru. yandex.ru. 345600 IN NS ns4.yandex.ru. yandex.ru. 345600 IN NS ns5.yandex.ru. ;; Query time: 133 msec ;; SERVER: 195.149.70.20#53(195.149.70.20) ;; WHEN: Wed Dec 17 14:30:49 2008 ;; MSG SIZE rcvd: 163 |
|
#dig @ns.uz.gov.ua yandex.ru a
; <<>> DiG 9.5.0-P2 <<>> @ns.uz.gov.ua yandex.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 7191 ;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 4, ADDITIONAL: 0 ;; QUESTION SECTION: ;yandex.ru. IN A ;; ANSWER SECTION: yandex.ru. 10794 IN A 213.180.204.11 ... yandex.ru. 10794 IN A 93.158.134.11 ;; AUTHORITY SECTION: yandex.ru. 345594 IN NS ns5.yandex.ru. yandex.ru. 345594 IN NS ns1.yandex.ru. yandex.ru. 345594 IN NS ns2.yandex.ru. yandex.ru. 345594 IN NS ns4.yandex.ru. ;; Query time: 10 msec ;; SERVER: 195.149.70.20#53(195.149.70.20) ;; WHEN: Wed Dec 17 14:30:55 2008 ;; MSG SIZE rcvd: 163 |
|
#dig @ns.uz.gov.ua uz.gov.ua axfr
; <<>> DiG 9.5.0-P2 <<>> @ns.uz.gov.ua uz.gov.ua axfr ; (1 server found) ;; global options: printcmd ; Transfer failed. |
|
#dig @ns1.uz.gov.ua uz.gov.ua axfr

dig: couldn't get address for 'ns1.uz.gov.ua': not found |
|
#dig @ns2.uz.gov.ua uz.gov.ua axfr
; <<>> DiG 9.5.0-P2 <<>> @ns2.uz.gov.ua uz.gov.ua axfr ; (1 server found) ;; global options: printcmd uz.gov.ua. 10800 IN SOA ns.uz.gov.ua. hostmaster.uz.gov.ua. 2008102301 28800 14400 864000 86400 uz.gov.ua. 10800 IN A 195.149.70.27 uz.gov.ua. 10800 IN MX 10 relay.uz.gov.ua. uz.gov.ua. 10800 IN NS ns.uz.gov.ua. uz.gov.ua. 10800 IN NS ns.secondary.net.ua. uz.gov.ua. 10800 IN NS ns2.uz.gov.ua. cargo.uz.gov.ua. 10800 IN A 195.149.70.27 ... www.uz.gov.ua. 10800 IN A 195.149.70.27 zp.uz.gov.ua. 10800 IN NS ns.uz.gov.ua. zp.uz.gov.ua. 10800 IN NS ns.zp.uz.gov.ua. zp.uz.gov.ua. 10800 IN NS ns2.uz.gov.ua. ns.zp.uz.gov.ua. 10800 IN A 193.108.46.123 uz.gov.ua. 10800 IN SOA ns.uz.gov.ua. hostmaster.uz.gov.ua. 2008102301 28800 14400 864000 86400 ;; Query time: 176 msec ;; SERVER: 195.149.70.30#53(195.149.70.30) ;; WHEN: Wed Dec 17 15:02:03 2008 ;; XFR size: 64 records (messages 1, bytes 1351) |
|
#dig @ns2.uz.gov.ua uz.gov.ua axfr | less
|
|
#nc ox.uz.gov.ua 22

|
|
#whois 195.149.70.30
% This is the RIPE Whois query server #1. % The objects are in RPSL format. % % Rights restricted by copyright. % See http://www.ripe.net/db/copyright.html % Note: This output has been filtered. % To receive output for a database update, use the "-B" flag. % Information related to '195.149.70.0 - 195.149.70.255' inetnum: 195.149.70.0 - 195.149.70.255 netname: UZ-GOV-UA ... tech-c: AP986-RIPE nic-hdl: TMIC1-RIPE mnt-by: UZ-GOV-UA-MNT source: RIPE # Filtered % Information related to '195.149.70.0/24AS29325' route: 195.149.70.0/24 descr: UZ-GOV-UA origin: AS29325 mnt-by: UZ-GOV-UA-MNT source: RIPE # Filtered |
|
#nmap -p22 195.149.70.0/24

Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 15:04 UTC |
|
#nmap -p22 195.149.70.0/24 | tee /tmp/uz
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 15:04 UTC Interesting ports on core.uz.gov.ua (195.149.70.1): PORT STATE SERVICE 22/tcp closed ssh Interesting ports on koliya1.uz.gov.ua (195.149.70.2): PORT STATE SERVICE 22/tcp filtered ssh Interesting ports on koliya2.uz.gov.ua (195.149.70.3): PORT STATE SERVICE 22/tcp filtered ssh ... Interesting ports on vpn2.uz.gov.ua (195.149.70.70): PORT STATE SERVICE 22/tcp closed ssh Interesting ports on info.uz.gov.ua (195.149.70.142): PORT STATE SERVICE 22/tcp filtered ssh Interesting ports on host146.uz.gov.ua (195.149.70.146): PORT STATE SERVICE 22/tcp filtered ssh Nmap done: 256 IP addresses (15 hosts up) scanned in 8.568 seconds |
|
#less /tmp/uz
|
|
#grep 195.149 /tmp/uz
Interesting ports on core.uz.gov.ua (195.149.70.1): Interesting ports on koliya1.uz.gov.ua (195.149.70.2): Interesting ports on koliya2.uz.gov.ua (195.149.70.3): Interesting ports on invader.uz.gov.ua (195.149.70.20): Interesting ports on wolf.uz.gov.ua (195.149.70.22): Interesting ports on ox.uz.gov.ua (195.149.70.23): Interesting ports on www.uz.gov.ua (195.149.70.27): Interesting ports on tender.uz.gov.ua (195.149.70.28): Interesting ports on ns2.uz.gov.ua (195.149.70.30): Interesting ports on null.uz.gov.ua (195.149.70.35): Interesting ports on host68.uz.gov.ua (195.149.70.68): Interesting ports on host69.uz.gov.ua (195.149.70.69): Interesting ports on vpn2.uz.gov.ua (195.149.70.70): Interesting ports on info.uz.gov.ua (195.149.70.142): Interesting ports on host146.uz.gov.ua (195.149.70.146): |
|
#grep 195.149 /tmp/uz | awk '{print $5}'
(195.149.70.1): (195.149.70.2): (195.149.70.3): (195.149.70.20): (195.149.70.22): (195.149.70.23): (195.149.70.27): (195.149.70.28): (195.149.70.30): (195.149.70.35): (195.149.70.68): (195.149.70.69): (195.149.70.70): (195.149.70.142): (195.149.70.146): |
|
#grep 195.149 /tmp/uz | awk '{print $5}' | tr -d '():'
195.149.70.1 195.149.70.2 195.149.70.3 195.149.70.20 195.149.70.22 195.149.70.23 195.149.70.27 195.149.70.28 195.149.70.30 195.149.70.35 195.149.70.68 195.149.70.69 195.149.70.70 195.149.70.142 195.149.70.146 |
|
#gqview

(gqview:6580): Gtk-WARNING **: cannot open display: |
|
#traceroute -I -n 195.149.70.22
traceroute to 195.149.70.22 (195.149.70.22), 30 hops max, 40 byte packets 1 10.0.35.1 0.178 ms 0.172 ms 0.166 ms 2 192.168.70.1 6.281 ms 44.307 ms 44.317 ms 3 194.150.93.65 44.320 ms 44.333 ms 44.341 ms 4 194.150.92.14 44.351 ms * * 5 * * * 6 * 195.35.65.225 232.265 ms 232.218 ms 7 80.91.186.194 77.841 ms 106.472 ms 92.306 ms 8 195.149.70.22 98.589 ms 98.521 ms 98.493 ms |
|
#whois 80.91.186.194
% This is the RIPE Whois query server #1. % The objects are in RPSL format. % % Rights restricted by copyright. % See http://www.ripe.net/db/copyright.html % Note: This output has been filtered. % To receive output for a database update, use the "-B" flag. % Information related to '80.91.186.0 - 80.91.186.255' inetnum: 80.91.186.0 - 80.91.186.255 netname: INTERCONNECTIONS-DATAGROUP ... descr: DATAGROUP aggregated block origin: AS21219 mnt-by: DATACOM-NOC source: RIPE # Filtered % Information related to '80.91.176.0/20AS21219' route: 80.91.176.0/20 descr: DATAGROUP aggregated block origin: AS21219 mnt-by: DATACOM-NOC source: RIPE # Filtered |
|
#host 80.91.186.194
Name: undefined.datagroup.com.ua Address: 80.91.186.194 |
|
#nc 80.91.186.194 3128

(UNKNOWN) [80.91.186.194] 3128 (?) : Connection refused |
|
#nmap -sS -O 80.91.186.194
Starting Nmap 4.68 ( http://nmap.org ) at 2008-12-17 15:10 UTC Stats: 0:00:07 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan SYN Stealth Scan Timing: About 46.45% done; ETC: 15:10 (0:00:07 remaining) Interesting ports on undefined.datagroup.com.ua (80.91.186.194): Not shown: 1711 closed ports PORT STATE SERVICE 25/tcp filtered smtp 1720/tcp open H.323/Q.931 5060/tcp open sip 5901/tcp open vnc-1 Device type: router|broadband router|switch|WAP Running (JUST GUESSING) : Cisco IOS 12.X|12.2 (93%), Cisco embedded (92%) Aggressive OS guesses: Cisco 1811 or 2800 router (IOS 12.4) (93%), Cisco 7200 Series router (93%), Cisco 827H ADSL router (92%), Cisco 837, 850-series, 870, 1801, 2600-series, 2800, 3800, or 7000-series router (IOS 12.4) (91%), Cisco Catalyst 6500 switch (IOS 12.2) (91%), Cisco 2620 router (IOS 12.3) (90%), Cisco Aironet 1200 WAP (IOS 12.3) (89%), Cisco 2509 router (IOS 12.3) (88%), Cisco 3560, 37 No exact OS matches for host (test conditions non-ideal). Network Distance: 7 hops OS detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 13.287 seconds |
|
#host 195.149.70.1
Name: core.uz.gov.ua Address: 195.149.70.1 |
|
#nc 195.149.70.1 22

(UNKNOWN) [195.149.70.1] 22 (ssh) : Connection refused |
|
#nc 195.149.70.1 25

|
|
#nc 195.149.70.1 80

(UNKNOWN) [195.149.70.1] 80 (www) : Connection refused |
|
#host 195.35.65.225
Name: datagroup-10G-gw.ix.net.ua Address: 195.35.65.225 |
|
#apt-get install dsniff
Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: python2.4-minimal python2.4 libttf2 cpp-4.2 Use 'apt-get autoremove' to remove them. The following extra packages will be installed: libnids1.21 The following NEW packages will be installed: dsniff libnids1.21 ... Get:1 http://10.0.35.1 sid/main libnids1.21 1.23-1 [24.8kB] Get:2 http://10.0.35.1 sid/main dsniff 2.4b1+debian-18 [119kB] Fetched 144kB in 0s (2112kB/s) Selecting previously deselected package libnids1.21. (Reading database ... 40855 files and directories currently installed.) Unpacking libnids1.21 (from .../libnids1.21_1.23-1_i386.deb) ... Selecting previously deselected package dsniff. Unpacking dsniff (from .../dsniff_2.4b1+debian-18_i386.deb) ... Setting up libnids1.21 (1.23-1) ... Setting up dsniff (2.4b1+debian-18) ... |
|
#dpkg -L dsniff | grep bin
/usr/sbin /usr/sbin/dsniff /usr/sbin/msgsnarf /usr/sbin/tcpnice /usr/sbin/sshow /usr/sbin/macof /usr/sbin/mailsnarf /usr/sbin/urlsnarf /usr/sbin/sshmitm /usr/sbin/arpspoof /usr/sbin/filesnarf /usr/sbin/webmitm /usr/sbin/dnsspoof /usr/sbin/tcpkill /usr/sbin/webspy |
|
#apt-get install xbill
Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: python2.4-minimal python2.4 libttf2 cpp-4.2 Use 'apt-get autoremove' to remove them. The following NEW packages will be installed: xbill 0 upgraded, 1 newly installed, 0 to remove and 370 not upgraded. Need to get 54.4kB of archives. After this operation, 471kB of additional disk space will be used. Get:1 http://10.0.35.1 sid/main xbill 2.1-7 [54.4kB] Fetched 54.4kB in 0s (590kB/s) Selecting previously deselected package xbill. (Reading database ... 40899 files and directories currently installed.) Unpacking xbill (from .../archives/xbill_2.1-7_i386.deb) ... Setting up xbill (2.1-7) ... |
|
#ping 192.168.15.31
PING 192.168.15.31 (192.168.15.31) 56(84) bytes of data. 64 bytes from 192.168.15.31: icmp_seq=1 ttl=63 time=0.258 ms --- 192.168.15.31 ping statistics --- 1 packets transmitted, 1 received, 0% packet loss, time 0ms rtt min/avg/max/mdev = 0.258/0.258/0.258/0.000 ms |
|
#dig @192.168.15.31 ya.ru a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ya.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 7692 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 0 ;; QUESTION SECTION: ;ya.ru. IN A ;; ANSWER SECTION: ya.ru. 7200 IN A 213.180.204.8 ;; AUTHORITY SECTION: ya.ru. 7200 IN NS ns5.yandex.ru. ya.ru. 7200 IN NS ns1.yandex.ru. ;; Query time: 489 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:37:32 2008 ;; MSG SIZE rcvd: 82 |
|
#dig @192.168.15.31 ya.ru a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ya.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 57217 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 0 ;; QUESTION SECTION: ;ya.ru. IN A ;; ANSWER SECTION: ya.ru. 7141 IN A 213.180.204.8 ;; AUTHORITY SECTION: ya.ru. 7141 IN NS ns5.yandex.ru. ya.ru. 7141 IN NS ns1.yandex.ru. ;; Query time: 1 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:38:31 2008 ;; MSG SIZE rcvd: 82 |
|
#dig @192.168.15.31 yandex.ru a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 yandex.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 13258 ;; flags: qr rd ra; QUERY: 1, ANSWER: 4, AUTHORITY: 4, ADDITIONAL: 0 ;; QUESTION SECTION: ;yandex.ru. IN A ;; ANSWER SECTION: yandex.ru. 10800 IN A 77.88.21.11 ... yandex.ru. 10800 IN A 87.250.251.11 ;; AUTHORITY SECTION: yandex.ru. 345600 IN NS ns4.yandex.ru. yandex.ru. 345600 IN NS ns1.yandex.ru. yandex.ru. 345600 IN NS ns2.yandex.ru. yandex.ru. 345600 IN NS ns5.yandex.ru. ;; Query time: 129 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:38:42 2008 ;; MSG SIZE rcvd: 163 |
|
#dig @192.168.15.31 google.ru a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 google.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 11393 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 4, ADDITIONAL: 4 ;; QUESTION SECTION: ;google.ru. IN A ;; ANSWER SECTION: google.ru. 1800 IN A 72.14.221.104 ... google.ru. 345600 IN NS ns2.google.com. ;; ADDITIONAL SECTION: ns2.google.com. 172800 IN A 216.239.34.10 ns3.google.com. 172800 IN A 216.239.36.10 ns4.google.com. 172800 IN A 216.239.38.10 ns1.google.com. 172800 IN A 216.239.32.10 ;; Query time: 193 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:39:28 2008 ;; MSG SIZE rcvd: 221 |
|
#dig @192.168.15.31 kernel.org a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 kernel.org a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 1025 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 10, ADDITIONAL: 2 ;; QUESTION SECTION: ;kernel.org. IN A ;; ANSWER SECTION: kernel.org. 600 IN A 204.152.191.37 ... kernel.org. 86400 IN NS ns3.kernel.org. kernel.org. 86400 IN NS zeus1.kernel.org. kernel.org. 86400 IN NS ns1.kernel.org. ;; ADDITIONAL SECTION: zeus1.kernel.org. 600 IN A 149.20.20.132 zeus2.kernel.org. 600 IN A 204.152.191.36 ;; Query time: 528 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:41:13 2008 ;; MSG SIZE rcvd: 280 |
|
#dig @192.168.15.31 blogger.com a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 blogger.com a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 30891 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 4, ADDITIONAL: 4 ;; QUESTION SECTION: ;blogger.com. IN A ;; ANSWER SECTION: blogger.com. 3600 IN A 209.85.165.191 ... blogger.com. 345600 IN NS ns2.google.com. ;; ADDITIONAL SECTION: ns1.google.com. 172670 IN A 216.239.32.10 ns3.google.com. 172670 IN A 216.239.36.10 ns2.google.com. 172670 IN A 216.239.34.10 ns4.google.com. 172670 IN A 216.239.38.10 ;; Query time: 328 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:41:38 2008 ;; MSG SIZE rcvd: 220 |
|
#dig @192.168.15.31 i.ua a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 i.ua a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 27636 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 0 ;; QUESTION SECTION: ;i.ua. IN A ;; ANSWER SECTION: i.ua. 86400 IN A 91.198.36.14 ;; AUTHORITY SECTION: i.ua. 86400 IN NS ns1.i.ua. i.ua. 86400 IN NS ns2.i.ua. ;; Query time: 300 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:42:33 2008 ;; MSG SIZE rcvd: 74 |
|
#route -n
Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 10.0.0.0 0.0.0.0 255.0.0.0 U 0 0 0 eth0 0.0.0.0 10.0.35.1 0.0.0.0 UG 0 0 0 eth0 |
|
#dig @192.168.15.31 meta.ua a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 meta.ua a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 32294 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;meta.ua. IN A ;; ANSWER SECTION: meta.ua. 43200 IN A 194.0.131.18 ;; AUTHORITY SECTION: meta.ua. 43200 IN NS ns.dns.com.ua. meta.ua. 43200 IN NS ns2.dns.com.ua. ;; ADDITIONAL SECTION: ns.dns.com.ua. 3600 IN A 62.149.2.8 ns2.dns.com.ua. 3600 IN A 195.149.112.1 ;; Query time: 449 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:45:24 2008 ;; MSG SIZE rcvd: 116 |
|
#dig @192.168.15.31 ukr.net a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ukr.net a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 17207 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;ukr.net. IN A ;; ANSWER SECTION: ukr.net. 600 IN A 195.214.195.105 ;; AUTHORITY SECTION: ukr.net. 86400 IN NS ns.ukr.net.ua. ukr.net. 86400 IN NS nss.ukr.net.ua. ;; ADDITIONAL SECTION: nss.ukr.net.ua. 86400 IN A 212.42.64.9 ns.ukr.net.ua. 86400 IN A 212.42.64.7 ;; Query time: 539 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:46:21 2008 ;; MSG SIZE rcvd: 118 |
|
#dig @192.168.15.31 ukr.net a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ukr.net a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 58736 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 2, ADDITIONAL: 2 ;; QUESTION SECTION: ;ukr.net. IN A ;; ANSWER SECTION: ukr.net. 465 IN A 195.214.195.105 ;; AUTHORITY SECTION: ukr.net. 86265 IN NS ns.ukr.net.ua. ukr.net. 86265 IN NS nss.ukr.net.ua. ;; ADDITIONAL SECTION: nss.ukr.net.ua. 86265 IN A 212.42.64.9 ns.ukr.net.ua. 86265 IN A 212.42.64.7 ;; Query time: 1 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:48:36 2008 ;; MSG SIZE rcvd: 118 |
|
#dig @192.168.15.31 ua.fm a

; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ua.fm a ; (1 server found) ;; global options: printcmd ;; connection timed out; no servers could be reached |
|
#ping 192.168.15.31
PING 192.168.15.31 (192.168.15.31) 56(84) bytes of data. 64 bytes from 192.168.15.31: icmp_seq=1 ttl=63 time=0.378 ms --- 192.168.15.31 ping statistics --- 1 packets transmitted, 1 received, 0% packet loss, time 0ms rtt min/avg/max/mdev = 0.378/0.378/0.378/0.000 ms |
|
#dig @192.168.15.31 ua.fm a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ua.fm a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 56359 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;ua.fm. IN A ;; Query time: 1 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:50:30 2008 ;; MSG SIZE rcvd: 23 |
|
#dig @192.168.15.31 ua.fm a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ua.fm a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 52812 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;ua.fm. IN A ;; Query time: 2 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:50:32 2008 ;; MSG SIZE rcvd: 23 |
|
#dig @192.168.15.31 ua.fm a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ua.fm a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 40951 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;ua.fm. IN A ;; Query time: 1 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:51:13 2008 ;; MSG SIZE rcvd: 23 |
|
#dig @192.168.15.31 ua.fm a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ua.fm a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 14962 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;ua.fm. IN A ;; Query time: 2 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:51:14 2008 ;; MSG SIZE rcvd: 23 |
|
#dig @192.168.15.31 ua.fm a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ua.fm a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 42673 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;ua.fm. IN A ;; Query time: 1 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:51:44 2008 ;; MSG SIZE rcvd: 23 |
|
#dig @192.168.15.31 ua.fm a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ua.fm a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 17560 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;ua.fm. IN A ;; Query time: 1 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:51:50 2008 ;; MSG SIZE rcvd: 23 |
|
#dig @192.168.15.31 ua.fm a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ua.fm a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 6420 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;ua.fm. IN A ;; Query time: 1 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:51:53 2008 ;; MSG SIZE rcvd: 23 |
|
#dig @192.168.15.31 ya.ru a
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ya.ru a ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 35252 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;ya.ru. IN A ;; Query time: 1 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Wed Dec 17 15:51:56 2008 ;; MSG SIZE rcvd: 23 |
|
#dig @192.168.15.31 ya.ru a10.1010
; <<>> DiG 9.5.0-P2 <<>> @192.168.15.31 ya.ru a10.1010 ; (1 server found) ;; global options: printcmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 7102 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;ya.ru. IN A ;; Query time: 1 msec ... ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 39030 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0 ;; WARNING: recursion requested but not available ;; QUESTION SECTION: ;a10.1010. IN A ;; Query time: 0 msec ;; SERVER: 192.168.15.31#53(192.168.15.31) ;; WHEN: Thu Dec 18 08:12:52 2008 ;; MSG SIZE rcvd: 26 |
|
#ping 10.0.35.70

PING 10.0.35.70 (10.0.35.70) 56(84) bytes of data. --- 10.0.35.70 ping statistics --- 3 packets transmitted, 0 received, 100% packet loss, time 2000ms |
|
#route -n
Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 10.0.0.0 0.0.0.0 255.0.0.0 U 0 0 0 eth0 0.0.0.0 10.0.35.1 0.0.0.0 UG 0 0 0 eth0 |
|
#ping ya.ru

PING ya.ru (213.180.204.8) 56(84) bytes of data. --- ya.ru ping statistics --- 5 packets transmitted, 0 received, 100% packet loss, time 4009ms |
|
#top

top - 10:29:30 up 1 day, 1:51, 4 users, load average: 0.50, 0.18, 0.06
Tasks: 70 total, 1 running, 69 sleeping, 0 stopped, 0 zombie
Cpu(s): 19.5%us, 1.7%sy, 0.0%ni, 78.9%id, 0.0%wa, 0.0%hi, 0.0%si, 0.0%st
Mem: 409748k total, 388440k used, 21308k free, 35596k buffers
PID USER PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
Swap: 0k total, 0k used, 0k free, 109732k cached
1732 root 16 0 7876 5880 1516 S 19.0 1.4 0:37.94 l3-agent
5550 root 15 0 41032 37m 4448 S 1.7 9.4 1:46.89 Xvnc
1 root 15 0 2100 676 580 S 0.0 0.2 0:00.03 init
2 root RT 0 0 0 0 S 0.0 0.0 0:00.00 migration/0
...
6 root 10 -5 0 0 0 S 0.0 0.0 0:00.00 kthread
7 root 20 -5 0 0 0 S 0.0 0.0 0:00.00 xenwatch
8 root 15 -5 0 0 0 S 0.0 0.0 0:00.00 xenbus
14 root 10 -5 0 0 0 S 0.0 0.0 0:00.00 kblockd/0
14 root 10 -5 0 0 0 S 0.0 0.0 0:00.00 kblockd/0
16 root 20 -5 0 0 0 S 0.0 0.0 0:00.00 kseriod
53 root 15 0 0 0 0 S 0.0 0.0 0:00.00 pdflush
54 root 15 0 0 0 0 S 0.0 0.0 0:00.01 pdflush
55 root 10 -5 0 0 0 S 0.0 0.0 0:00.03 kswapd0
56 root 20 -5 0 0 0 S 0.0 0.0 0:00.00 aio/0
|
|
#ping 10.0.35.70
PING 10.0.35.70 (10.0.35.70) 56(84) bytes of data. 64 bytes from 10.0.35.70: icmp_seq=1 ttl=64 time=2.38 ms 64 bytes from 10.0.35.70: icmp_seq=2 ttl=64 time=0.217 ms --- 10.0.35.70 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1001ms rtt min/avg/max/mdev = 0.217/1.302/2.388/1.086 ms |
|
#ssh root@10.0.35.70

libxml2 libxmu6 libxmuu1 libxpm4 libxrandr2 libxrender1 libxres1 libxt6 libxtrap6 libxtst6 libxv1 libxxf86dga1 libxxf86misc1 libxxf86vm1 lpr mime-support miscfiles myspell-en-us notification-daemon orage pciutils perl perl-doc perl-modules pm-utils portmap powermgmt-base psfontmgr psmisc psutils python python-minimal python2.5 python2.5-minimal radeontool sgml-base shared-mime-info thunar thunar-data ttf-dejavu ttf-dejavu-core ttf-dejavu-extra ucf udev usbutils uswsusp vbetool wdiff x-ttcidfont-conf x11-apps x11-common x11-session-utils x11-utils x11-xfs-utils x11-xkb-utils x11-xserver-utils xauth xbase-clients xbitmaps xfce4 xfce4-icon-theme xfce4-mcs-manager xfce4-mcs-plugins xfce4-mixer xfce4-mixer-alsa xfce4-panel xfce4-session xfce4-terminal xfce4-utils xfdesktop4 xfdesktop4-data |
|
#ssh 10.0.100.10

speakup-modules-2.6.26-1-amd64 - Screen review module for Linux 2.6.26 on AMD64 speakup-modules-2.6.26-1-openvz-686 - Screen review module for Linux 2.6.26 on PPro/Celeron/PII/PIII/P4 speakup-modules-2.6.26-1-vserver-686 - Screen review module for Linux 2.6.26 on PPro/Celeron/PII/PIII/P4 speakup-modules-2.6.26-1-vserver-686-bigmem - Screen review module for Linux 2.6.26 on PPro/Celeron/PII/PIII/P4 speakup-modules-2.6.26-1-xen-686 - Screen review module for Linux 2.6.26 on i686 squashfs-modules-2.6.26-1-486 - Compression filesystem for Linux 2.6.26 on x86 squashfs-modules-2.6.26-1-686 - Compression filesystem for Linux 2.6.26 on PPro/Celeron/PII/PIII/P4 squashfs-modules-2.6.26-1-686-bigmem - Compression filesystem for Linux 2.6.26 on PPro/Celeron/PII/PIII/P4 squashfs-modules-2.6.26-1-amd64 - Compression filesystem for Linux 2.6.26 on AMD64 squashfs-modules-2.6.26-1-openvz-686 - Compression filesystem for Linux 2.6.26 on PPro/Celeron/PII/PIII/P4 ... libc6-i686 linux-image-2.6.26-1-686 Suggested packages: linux-doc-2.6.26 The following NEW packages will be installed: libc6-i686 linux-image-2.6-686 linux-image-2.6.26-1-686 0 upgraded, 3 newly installed, 0 to remove and 0 not upgraded. Need to get 21.5MB of archives. After this operation, 62.3MB of additional disk space will be used. Do you want to continue [Y/n]? Get:1 http://10.0.35.1 sid/main linux-image-2.6.26-1-686 2.6.26-12 [20.2MB] |
|
#t

l3script: t: command not found |
|
#ls
Desktop arp.log log.eci nt.com.ua tracemap.dot tracemap.png arp.dot arp.png log.ecp pic1.xcf tracemap.pl tracemap.svg |
|
#echo $PS1
|
|
#tty
/dev/pts/4 |
|
#script

script scriptreplay |
|
#script
script scriptreplay |
|
#ps aux | grep l3-ag
root 1732 0.5 1.4 8004 5956 ? Ss Dec17 10:03 l3-agent root 8594 0.0 0.1 1848 520 pts/5 R+ 15:11 0:00 grep l3-ag |
|
#which l3-agent
/usr/local/bin/l3-agent |
|
#less `!!`
|
|
#apt-get install snmp
Reading package lists... Done Building dependency tree Reading state information... Done The following packages were automatically installed and are no longer required: python2.4-minimal python2.4 libttf2 cpp-4.2 Use 'apt-get autoremove' to remove them. The following extra packages will be installed: libperl5.10 libsensors3 libsnmp-base libsnmp15 Suggested packages: lm-sensors ... Unpacking libsnmp15 (from .../libsnmp15_5.4.1~dfsg-11_i386.deb) ... Selecting previously deselected package snmp. Unpacking snmp (from .../snmp_5.4.1~dfsg-11_i386.deb) ... Setting up libperl5.10 (5.10.0-18) ... Setting up libsensors3 (1:2.10.7-1) ... udev active, devices will be created in /dev/.static/dev/ Creating config file /etc/sensors.conf with new version Setting up libsnmp-base (5.4.1~dfsg-11) ... Setting up libsnmp15 (5.4.1~dfsg-11) ... Setting up snmp (5.4.1~dfsg-11) ... |
|
#snmpwalk -v2c -c public 81.30.160.3 .

RFC1213-MIB::ipRouteDest.79.143.41.114 = IpAddress: 79.143.41.114 RFC1213-MIB::ipRouteDest.79.143.41.126 = IpAddress: 79.143.41.126 RFC1213-MIB::ipRouteDest.79.143.41.130 = IpAddress: 79.143.41.130 RFC1213-MIB::ipRouteDest.79.143.41.134 = IpAddress: 79.143.41.134 RFC1213-MIB::ipRouteDest.79.143.41.138 = IpAddress: 79.143.41.138 RFC1213-MIB::ipRouteDest.79.143.41.142 = IpAddress: 79.143.41.142 RFC1213-MIB::ipRouteDest.79.143.41.146 = IpAddress: 79.143.41.146 RFC1213-MIB::ipRouteDest.79.143.41.150 = IpAddress: 79.143.41.150 RFC1213-MIB::ipRouteDest.79.143.41.154 = IpAddress: 79.143.41.154 RFC1213-MIB::ipRouteDest.79.143.41.158 = IpAddress: 79.143.41.158 ... RFC1213-MIB::ipRouteDest.81.30.161.41 = IpAddress: 81.30.161.41 RFC1213-MIB::ipRouteDest.81.30.161.43 = IpAddress: 81.30.161.43 RFC1213-MIB::ipRouteDest.81.30.161.45 = IpAddress: 81.30.161.45 RFC1213-MIB::ipRouteDest.81.30.161.46 = IpAddress: 81.30.161.46 RFC1213-MIB::ipRouteDest.81.30.161.55 = IpAddress: 81.30.161.55 RFC1213-MIB::ipRouteDest.81.30.161.56 = IpAddress: 81.30.161.56 RFC1213-MIB::ipRouteDest.81.30.161.57 = IpAddress: 81.30.161.57 RFC1213-MIB::ipRouteDest.81.30.161.65 = IpAddress: 81.30.161.65 RFC1213-MIB::ipRouteDest.81.30.161.67 = IpAddress: 81.30.161.67 RFC1213-MIB::ipRouteDest.81.30.161.70 = IpAddress: 81.30.161.70 |
|
#ping 81.30.160.3
PING 81.30.160.3 (81.30.160.3) 56(84) bytes of data. 64 bytes from 81.30.160.3: icmp_seq=1 ttl=58 time=14.5 ms 64 bytes from 81.30.160.3: icmp_seq=2 ttl=58 time=13.5 ms --- 81.30.160.3 ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 999ms rtt min/avg/max/mdev = 13.576/14.066/14.557/0.504 ms |
|
#snmpwalk -v2c -c public 81.30.160.3 .

SNMPv2-MIB::sysDescr.0 = STRING: FreeBSD leo.vinnitsa.com 4.6-RELEASE FreeBSD 4.6-RELEASE #0: Sat Aug i386 SNMPv2-MIB::sysObjectID.0 = OID: UCD-SNMP-MIB::unknown DISMAN-EVENT-MIB::sysUpTimeInstance = Timeticks: (4186890096) 484 days, 14:15:00.96 SNMPv2-MIB::sysContact.0 = STRING: admin@vinnitsa.com SNMPv2-MIB::sysName.0 = STRING: leo.vinnitsa.com SNMPv2-MIB::sysLocation.0 = STRING: Vinnitsa, Ukraine UA SNMPv2-MIB::sysORLastChange.0 = Timeticks: (4) 0:00:00.04 SNMPv2-MIB::sysORID.1 = OID: IF-MIB::ifMIB SNMPv2-MIB::sysORID.2 = OID: SNMPv2-MIB::snmpMIB SNMPv2-MIB::sysORID.3 = OID: TCP-MIB::tcpMIB ... SNMPv2-MIB::sysORUpTime.4 = Timeticks: (2) 0:00:00.02 SNMPv2-MIB::sysORUpTime.5 = Timeticks: (2) 0:00:00.02 SNMPv2-MIB::sysORUpTime.6 = Timeticks: (2) 0:00:00.02 SNMPv2-MIB::sysORUpTime.7 = Timeticks: (4) 0:00:00.04 SNMPv2-MIB::sysORUpTime.8 = Timeticks: (4) 0:00:00.04 SNMPv2-MIB::sysORUpTime.9 = Timeticks: (4) 0:00:00.04 IF-MIB::ifNumber.0 = INTEGER: 7 IF-MIB::ifIndex.1 = INTEGER: 1 IF-MIB::ifIndex.2 = INTEGER: 2 IF-MIB::ifIndex.3 = INTEGER: 3 |
|
#ls *png
arp.png tracemap.png |
|
#cd /home/user
|
|
#ls *png
arp-spoofing.png ipfw.png spasibo.png arp.png iptables-filter.png suid.png dns-spoof.png iptables-nat.png syslog-deps.png dns-spoofing-external.png nessus.png syslog-ng.png flower.png rdp-mx.png vi.png halp-open-scan.png rmrf.png vms-and-vlans.png ids-network-part.png snort.png yersinia.png |
|
#l3mass_upload snort.png nessus.png
Uploaded file name is 2728266053103031822-1229503882_1229675193_snort.png Upload complete /var/www/xguru/l3shot/2728266053103031822-1229503882_1229675193_snort.png Uploaded file name is 2728266053103031822-1229503882_1229675194_nessus.png Upload complete /var/www/xguru/l3shot/2728266053103031822-1229503882_1229675194_nessus.png 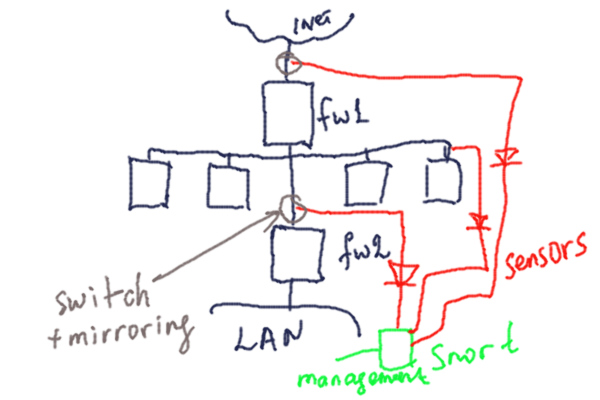 |
|
#apt-cache stats
Total package names : 34423 (1377k) Normal packages: 26344 Pure virtual packages: 1386 Single virtual packages: 1396 Mixed virtual packages: 522 Missing: 4775 Total distinct versions: 40625 (2112k) Total Distinct Descriptions: 40625 (975k) Total dependencies: 260853 (7304k) Total ver/file relations: 42693 (683k) Total Desc/File relations: 40625 (650k) Total Provides mappings: 7867 (157k) Total globbed strings: 45 (317) Total dependency version space: 1062k Total slack space: 84.6k Total space accounted for: 11.7M 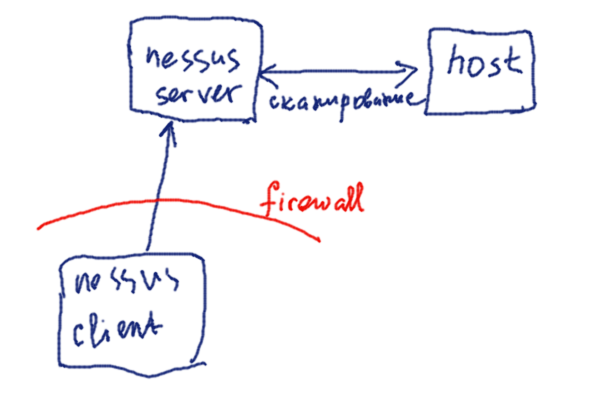 |
|
#apt-cache search snort
acidbase - Basic Analysis and Security Engine acidlab - Analysis Console for Intrusion Databases fwsnort - Snort-to-iptables rule translator ippl - IP protocols logger libprelude-dev - Hybrid Intrusion Detection System [ Development files ] libprelude-perl - Hybrid Intrusion Detection System [ Base library ] libprelude2 - Hybrid Intrusion Detection System [ Base library ] libprelude2-dbg - Hybrid Intrusion Detection System [ Debug symbols ] libpreludedb-dev - Hybrid Intrusion Detection System [ Development files ] libpreludedb-perl - Hybrid Intrusion Detection System [ Base library ] ... python-preludedb - Hybrid Intrusion Detection System [ Base library ] snort - flexible Network Intrusion Detection System snort-common - flexible Network Intrusion Detection System [common files] snort-common-libraries - flexible Network Intrusion Detection System ruleset snort-doc - Documentation for the Snort IDS [documentation] snort-mysql - flexible Network Intrusion Detection System [MySQL] snort-pgsql - flexible Network Intrusion Detection System [PostgreSQL] snort-rules-default - flexible Network Intrusion Detection System ruleset wflogs - The modular firewall log analyzer of the WallFire project airsnort - WLAN sniffer |
|
#l3mass_upload snort-distributed.png

Uploaded file name is 2728266053103031822-1229503882_1229678615_snort-distributed.png |
|
#ls
arp.dot arp.png log.eci nt.com.ua tracemap.dot tracemap.png arp.log Desktop log.ecp pic1.xcf tracemap.pl tracemap.svg |
|
#cd /home/user/
|
|
#ls
akula.xcf osdn2008-xen-drbd-chubin arp.png osdn2008-xen-drbd-chubin.tar.bz2 arp-spoofing.png osdn2008-xen-drbd-chubin.tar.bz2.1 Desktop rdp-mx.png dns-spoofing-external.png rmrf.png dns-spoofing-external.xcf snort-distributed.png dns-spoof.png snort.png flower.png spasibo.png gnu-screen.xcf start.xcf halp-open-scan.png suid.png ids-network-part.png syslog-deps.png ids-network-part.xcf syslog-ng.png ipfw.png syslog.xcf iptables-filter.png uploaded iptables-filter.xcf upload_xcf iptables-nat.png vi.png nessus.png vms-and-vlans.png one-server-for-one-service.xcf yersinia.png |
| Время первой команды журнала | 16:12:56 2008-12-17 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Время последней команды журнала | 18:51:16 2008-12-19 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Количество командных строк в журнале | 101 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Процент команд с ненулевым кодом завершения, % | 14.85 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Процент синтаксически неверно набранных команд, % | 1.98 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Суммарное время работы с терминалом *, час | 2.21 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Количество командных строк в единицу времени, команда/мин | 0.76 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Частота использования команд |
|
В журнал автоматически попадают все команды, данные в любом терминале системы.
Для того чтобы убедиться, что журнал на текущем терминале ведётся, и команды записываются, дайте команду w. В поле WHAT, соответствующем текущему терминалу, должна быть указана программа script.
Команды, при наборе которых были допущены синтаксические ошибки, выводятся перечёркнутым текстом:
$ l s-l bash: l: command not found |
Если код завершения команды равен нулю, команда была выполнена без ошибок. Команды, код завершения которых отличен от нуля, выделяются цветом.
$ test 5 -lt 4 |
Команды, ход выполнения которых был прерван пользователем, выделяются цветом.
$ find / -name abc find: /home/devi-orig/.gnome2: Keine Berechtigung find: /home/devi-orig/.gnome2_private: Keine Berechtigung find: /home/devi-orig/.nautilus/metafiles: Keine Berechtigung find: /home/devi-orig/.metacity: Keine Berechtigung find: /home/devi-orig/.inkscape: Keine Berechtigung ^C |
Команды, выполненные с привилегиями суперпользователя, выделяются слева красной чертой.
# id uid=0(root) gid=0(root) Gruppen=0(root) |
Изменения, внесённые в текстовый файл с помощью редактора, запоминаются и показываются в журнале в формате ed. Строки, начинающиеся символом "<", удалены, а строки, начинающиеся символом ">" -- добавлены.
$ vi ~/.bashrc
|
Для того чтобы изменить файл в соответствии с показанными в диффшоте изменениями, можно воспользоваться командой patch. Нужно скопировать изменения, запустить программу patch, указав в качестве её аргумента файл, к которому применяются изменения, и всавить скопированный текст:
$ patch ~/.bashrc |
Для того чтобы получить краткую справочную информацию о команде, нужно подвести к ней мышь. Во всплывающей подсказке появится краткое описание команды.
Если справочная информация о команде есть, команда выделяется голубым фоном, например: vi. Если справочная информация отсутствует, команда выделяется розовым фоном, например: notepad.exe. Справочная информация может отсутствовать в том случае, если (1) команда введена неверно; (2) если распознавание команды LiLaLo выполнено неверно; (3) если информация о команде неизвестна LiLaLo. Последнее возможно для редких команд.
Большие, в особенности многострочные, всплывающие подсказки лучше всего показываются браузерами KDE Konqueror, Apple Safari и Microsoft Internet Explorer. В браузерах Mozilla и Firefox они отображаются не полностью, а вместо перевода строки выводится специальный символ.
Время ввода команды, показанное в журнале, соответствует времени начала ввода командной строки, которое равно тому моменту, когда на терминале появилось приглашение интерпретатора
Имя терминала, на котором была введена команда, показано в специальном блоке. Этот блок показывается только в том случае, если терминал текущей команды отличается от терминала предыдущей.
Вывод не интересующих вас в настоящий момент элементов журнала, таких как время, имя терминала и других, можно отключить. Для этого нужно воспользоваться формой управления журналом вверху страницы.
Небольшие комментарии к командам можно вставлять прямо из командной строки. Комментарий вводится прямо в командную строку, после символов #^ или #v. Символы ^ и v показывают направление выбора команды, к которой относится комментарий: ^ - к предыдущей, v - к следующей. Например, если в командной строке было введено:
$ whoami
user
$ #^ Интересно, кто я?в журнале это будет выглядеть так:
$ whoami
user
| Интересно, кто я? |
Если комментарий содержит несколько строк, его можно вставить в журнал следующим образом:
$ whoami
user
$ cat > /dev/null #^ Интересно, кто я?
Программа whoami выводит имя пользователя, под которым мы зарегистрировались в системе. - Она не может ответить на вопрос о нашем назначении в этом мире.В журнале это будет выглядеть так:
$ whoami user
|
Комментарии, не относящиеся непосредственно ни к какой из команд, добавляются точно таким же способом, только вместо симолов #^ или #v нужно использовать символы #=
1
2
3
4
Группы команд, выполненных на разных терминалах, разделяются специальной линией.
Под этой линией в правом углу показано имя терминала, на котором выполнялись команды.
Для того чтобы посмотреть команды только одного сенса,
нужно щёкнуть по этому названию.
LiLaLo (L3) расшифровывается как Live Lab Log.
Программа разработана для повышения эффективности обучения Unix/Linux-системам.
(c) Игорь Чубин, 2004-2008